Kubernetes Pentest
The NodeZero® Kubernetes Pentest runs from inside your Kubernetes cluster to test the security of your cluster by identifying security misconfigurations and weaknesses that exist in your cluster.
Why should I run a NodeZero Kubernetes Pentest? How to Run a Kubernetes Pentest
Why should I run a NodeZero Kubernetes Pentest?
NodeZero runs from inside your cluster to help simulate the scenario that an attacker has gained a foothold on your cluster.
The foothold could be because an attacker found a user's kubeconfig file in a git repository or maybe an attacker compromised a web application running inside a pod in your cluster.
By running the Kubernetes pentest from inside your cluster and fixing the identified weaknesses, your organization can reduce the risk of the risk and impact of these attacks against your Kubernetes cluster.
How to Run a Kubernetes Pentest
To conduct a Kubernetes Pentest against your cluster, you must first install the NodeZero Operator. The NodeZero Operator will be the launch point for all the Kubernetes Pentests you run against your cluster. You only need to install the operator once per cluster allowing you to continuously test the security of your Kubernetes clusters.
Once installed, the operator can be used to install a runner or a single pentest.
Install the NodeZero Operator
Installation Requirements:
The NodeZero Operator and Kubernetes Pentest is supported on Kubernetes Cluster versions 1.24.0 and above.
You will need to have a terminal with kubectl and helm installed. Make sure kubectl is configured to use the context of your Kubernetes cluster.
The NodeZero Operator will need access to the following domains over port 443/TCP (Horizon3.ai's NodeZero Gateway:
US-Based
- gateway.horizon3ai.com
- api.gateway.horizon3ai.com
- registry.gateway.horizon3ai.com
- interact.gateway.horizon3ai.com
EU-Based
- gateway.horizon3ai.eu
- api.gateway.horizon3ai.eu
- registry.gateway.horizon3ai.eu
- registry.gateway.horizon3ai.com
- interact.gateway.horizon3ai.eu
Does the NodeZero Gateway feature support the NodeZero Operator?
- The NodeZero Operator and NodeZero Kubernetes Pentests are supported by NodeZero Gateway.
1. Navigate to Kubernetes Operators
From the Pentest dropdown select Kubernetes Operators.
2. Create Operator
Click the + Create Operator button.
Input a descriptive name and click Submit.
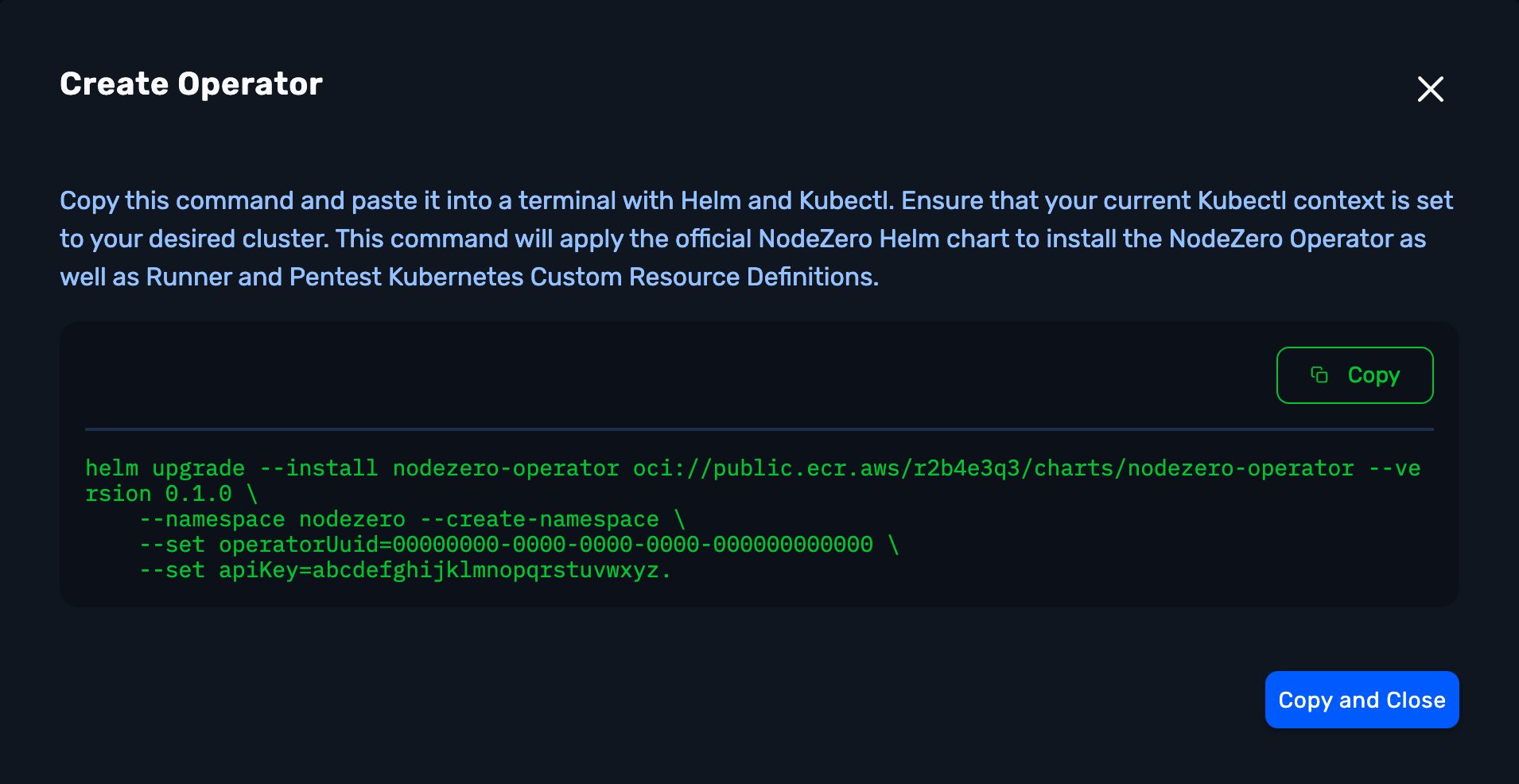
3. Install Operator
Follow the installation directions by copying the helm upgrade command and pasting into a terminal with Helm and Kubectl.
What permissions are needed to install the NodeZero Operator?
- An example ClusterRole CRD with the needed permissions can be found here.
Install a Kubernetes Runner
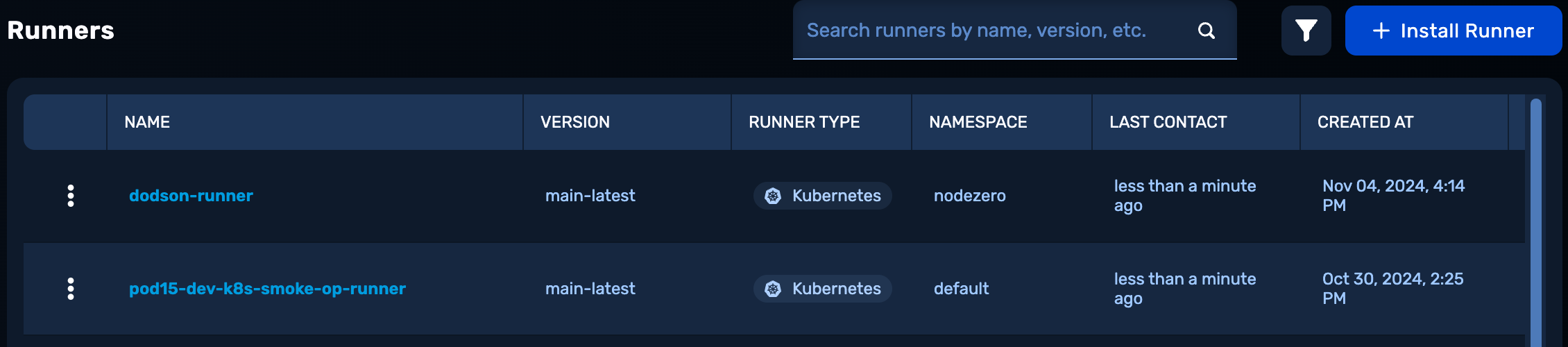
1. Navigate to Runners
From the Pentest dropdown select Runners.
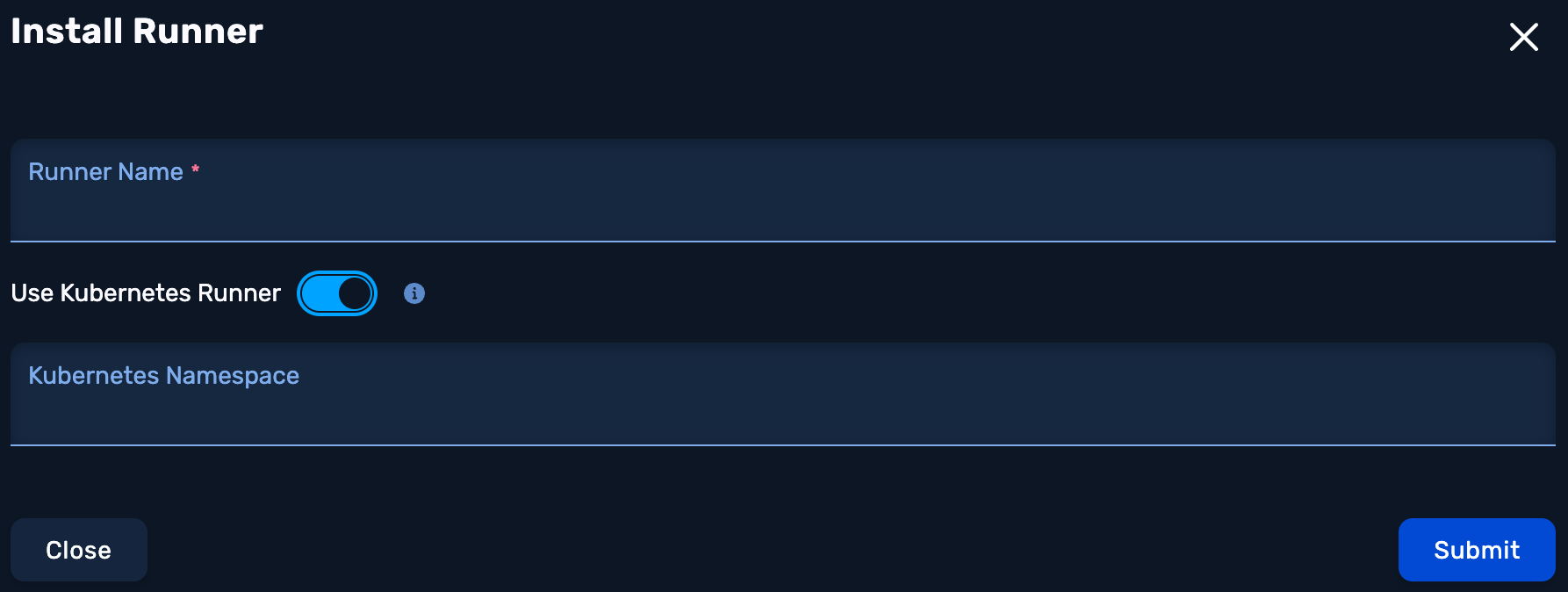
2. Create Runner
Click the Install Runner button.
Specify a name for the Runner, select the Use Kubernetes Runner toggle, specify a namespace, then click Submit.
Note
A Kubernetes Runner lives inside a namespace meaning any pentests that use that runner will run from that namespace. If desired, you can install a runner in each namespace.
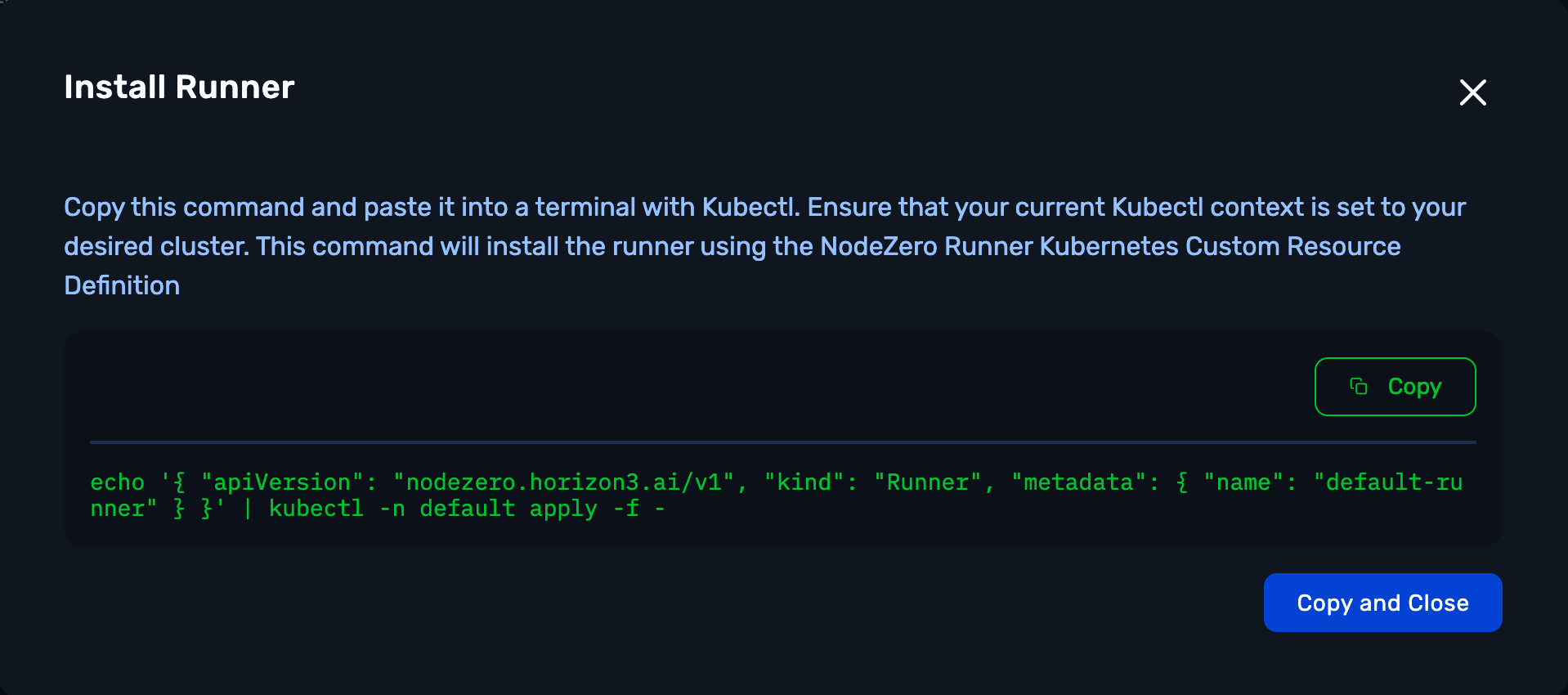
3. Install Runner
Copy this command and paste it into a terminal with Kubectl. Ensure that your current Kubectl context is set to your desired cluster. This one-time command will install the Runner using the NodeZero Runner Kubernetes Custom Resource Definition.
What permissions are needed to install the NodeZero runner?
- An example ClusterRole CRD with the needed permissions can be found here.
Run a Kubernetes Pentest
You can deploy NodeZero directly into any Kubernetes cluster, manage or self-managed, to pentest its security controls and vulnerabilities. Follow these steps to run a kubernetes pentest within your network.
1. Navigate to Pentests
Once you've installed a NodeZero Operator in your cluster, navigate to Pentests to start a Kubernetes pentest.
2. Click + Run Pentest
Click + Run Pentest to open Test Categories screen, and select Kubernetes Pentest from the "Infrastructure Attack Surface" category.
3. Configure the Kubernetes Pentest
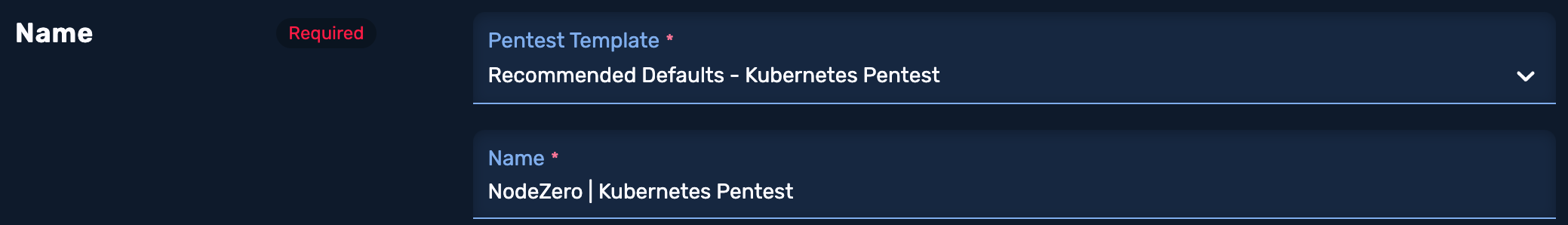
3.1 Name the Kubernetes Pentest
Name the Kubernetes Pentest and select a pentest template.
Determine and follow a naming convention to allow you to quickly find a pentest from your pentest list.
An example: [date]|[library]|[NodeZero Src]|[scope]
2021-09-01|NodeZero|East-Coast-Bizops-Cluster|Full: This indicates that the NodeZero host was placed in the East Coast Bizops cluster and the cluster CIDR ranges were explicitly added to scope.
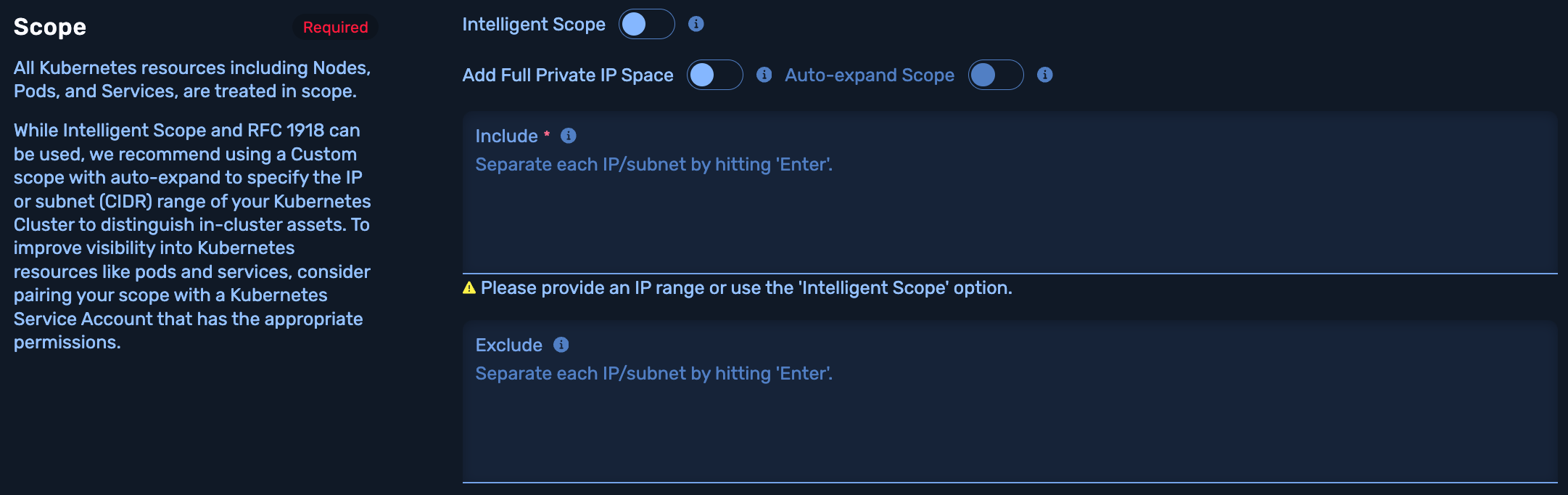
3.2 Select the Kubernetes Scope
Since the goal of the Kubernetes Pentest is to test your cluster, all Kubernetes resources are treated in scope including nodes, pods, and services. This means you cannot exclude any Kubernetes resources from testing.
The Kubernetes pentest scope is a set of IPs and/or subnets (in CIDR notation) that you explicitly want NodeZero to test.
Depending on where your NodeZero host is deployed, reachability to the provided scope can be affected by how much privilege, access, and authentication NodeZero can capture or is given.
Unlike vulnerability tools that scan for device fingerprints and services, NodeZero enumerates devices in scope and then chains together context, exploitable vulnerabilities, misconfiguration, insecure or weak controls, and any data or loot that it captures, to identify attack paths by priority of impact while providing proof. Typically, the larger the scope, the more findings you'll see, as NodeZero has much more to chain together.
There are three options for the Include section (defined below):
- Intelligent Scope
- Full RFC 1918 (192.168.0.0/16, 172.16.10.0/24, 10.0.0.0/8)
- Custom IP(s) or Subnet(s)
- Auto-expand (Optional)
While Intelligent Scope and RFC 1918 can be used, we recommend using a Custom scope with auto-expand to specify the IP or subnet (CIDR) range of your Kubernetes Cluster to distinguish in-cluster assets. Without specifying this NodeZero has a hard time determining what is inside or outside your cluster and therefore what is in scope and should be tested. To improve visibility into Kubernetes resources like pods and services, consider pairing your scope with a Kubernetes Service Account that has the appropriate permissions.
We also recommend providing the CIDR ranges of the internal network or VPC that your cluster resides in to see if NodeZero can reach outside the cluster to your other hosts.
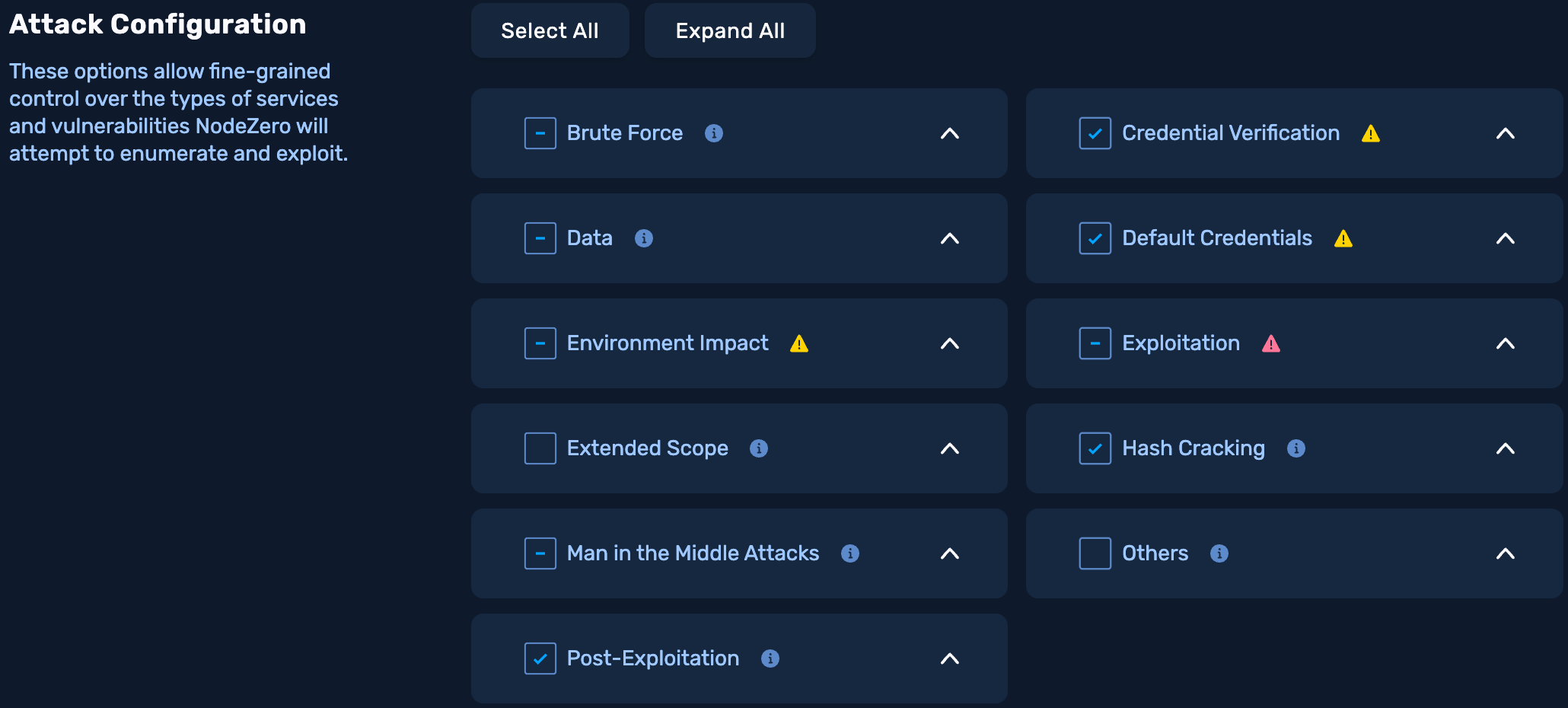
3.3 Attack Configuration
Select the types of services and vulnerabilities NodeZero will attempt to enumerate and exploit. For more information on choosing attack configuration options, visit the attack configuration options page.
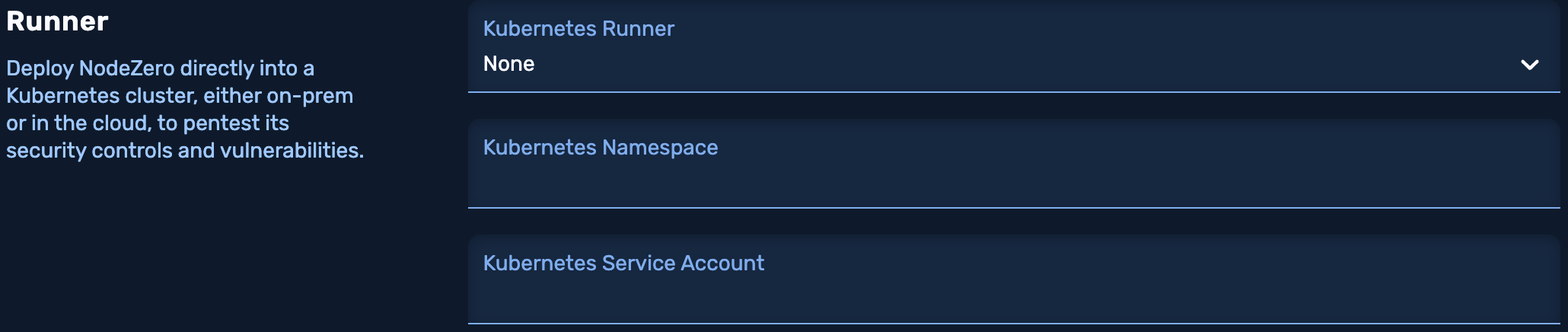
3.4 Runner
If you would like to deploy the pentest using a runner, feel free to select one! Please note that Kubernetes pentests can only use Kubernetes runners.
3.5 Kubernetes Settings
You can specify a Kubernetes Namespace and a Kubernetes Service Account that you would like NodeZero to use.
These are powerful settings that enable you to simulate the scenario where an attacker compromises a pod in your cluster.
To simulate this scenario simply specify the namespace and service account that one of your pods is configured with.
We recommend simulating pods that have ports accessible from outside the cluster as this is one of the more likely entry points for an attacker into your cluster.
Note
Since a Kubernetes runner lives inside a namespace, when you select a runner the pentest must run from that namespace, and you will not be able to customize that field.
3.6 Review the Kubernetes Pentest Configuration
Once satisfied with your pentest selections, check the box to indicate you've reviewed all advanced configuration settings. Then click Run Pentest, which launches the Kubernetes pentest.
4. Deploy NodeZero
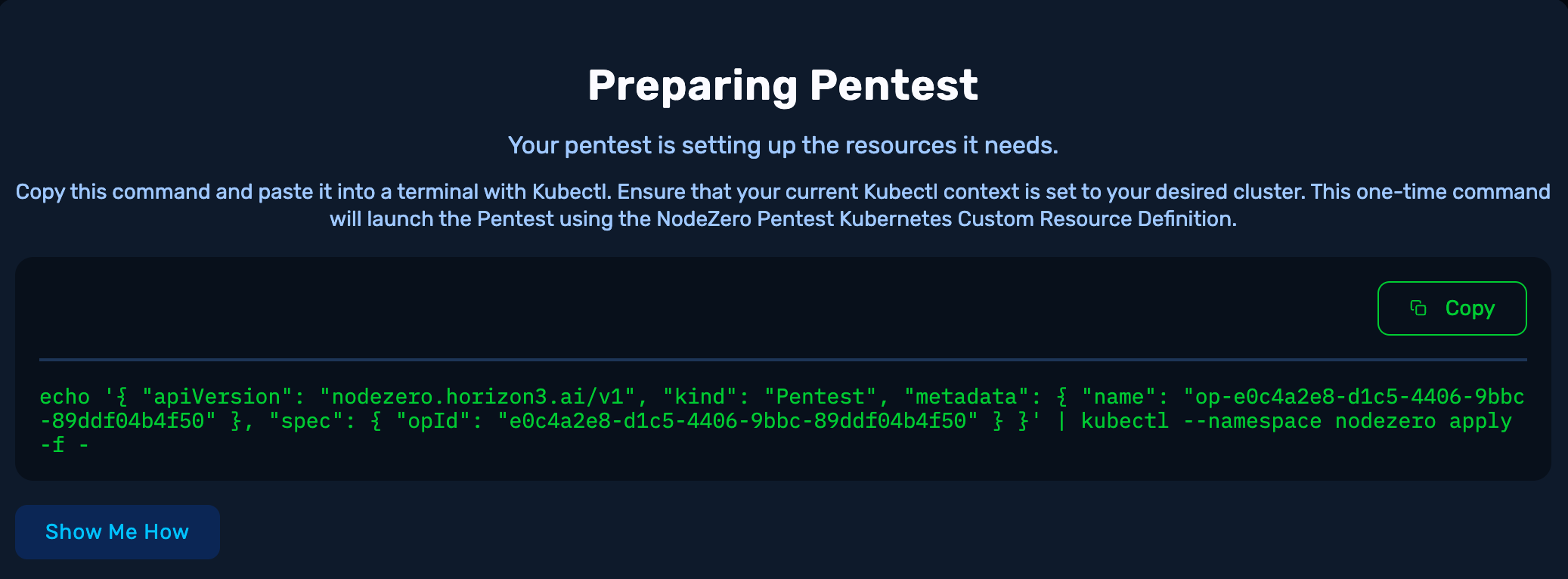
While the pentest is provisioning, its companion one-time-use software module, NodeZero, is made ready for deployment on your NodeZero Host.
Copy this command and paste it into a terminal with Kubectl. Ensure that your current Kubectl context is set to your desired cluster. This one-time command will launch the Pentest using the NodeZero Pentest Kubernetes Custom Resource Definition.
What permissions are needed to deploy the pentest?
- An example ClusterRole CRD with the needed permissions can be found here.
Real-Time View will show up, from where you can Inject Credentials and monitor pentest progress.
You've started a Kubernetes Pentest
NodeZero sends an email once the Kubernetes Pentest completes.