2023.08
Enhanced Proxy Support in NodeZero®
Proxy settings have been shifted from the NodeZero configuration directly to the host's Docker layer. This means once you set up the proxy configuration, all subsequent operations on that host will use these proxy settings until you decide to change them back.
The simplest method to adjust these settings is via the OVA. We've designed the NodeZero helper script to easily set up proxy settings once you supply the proxy string. If you're looking to configure the proxy outside of the OVA, please visit Using a Proxy with NodeZero for guidance.
Expanded Coercion Methods for Authentication in NodeZero
We've introduced ShadowCoerce, DFSCoerce, and Printerbug to NodeZero, enriching the available options for leveraging PetitPotam exploits. Coercion methods empower attackers to compel a domain controller to authenticate against an attacker-owned server. This subsequently allows the relaying of authentication materials to services that may be susceptible to this vulnerability. By exploiting these methods, attackers could potentially take control over entire Windows domains.
Expand to view diagram
Diagram shows four steps that an attacker can take to take over a Windows domain.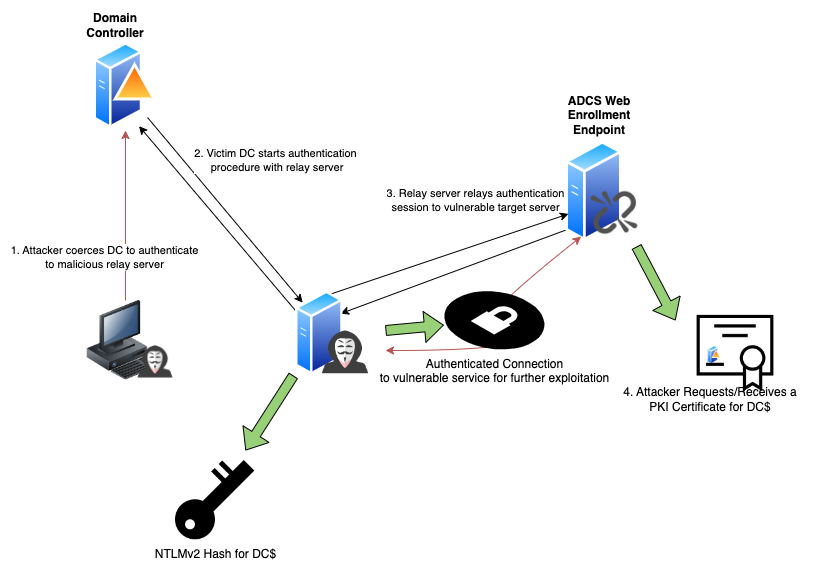
Extended Description
Improved Single Sign-On (SSO) Experience
Single Sign-On (SSO) is now available in open beta for all paid accounts!. Integrate with your preferred OIDC-compatible identity provider. To learn how to activate SSO for your account, refer to our SSO Documentation.
After enabling this feature, users can conveniently log in either directly through their identity provider or by simply clicking the 'Continue with Private SSO' button on the Portal's login page.
For early-access participants, we've enhanced the process, making it easier to provide the correct issuer URL. You now have the flexibility to modify or delete the provider, and retry the setup without requiring Horizon3 support!
Portal User Interface (UI) Updates
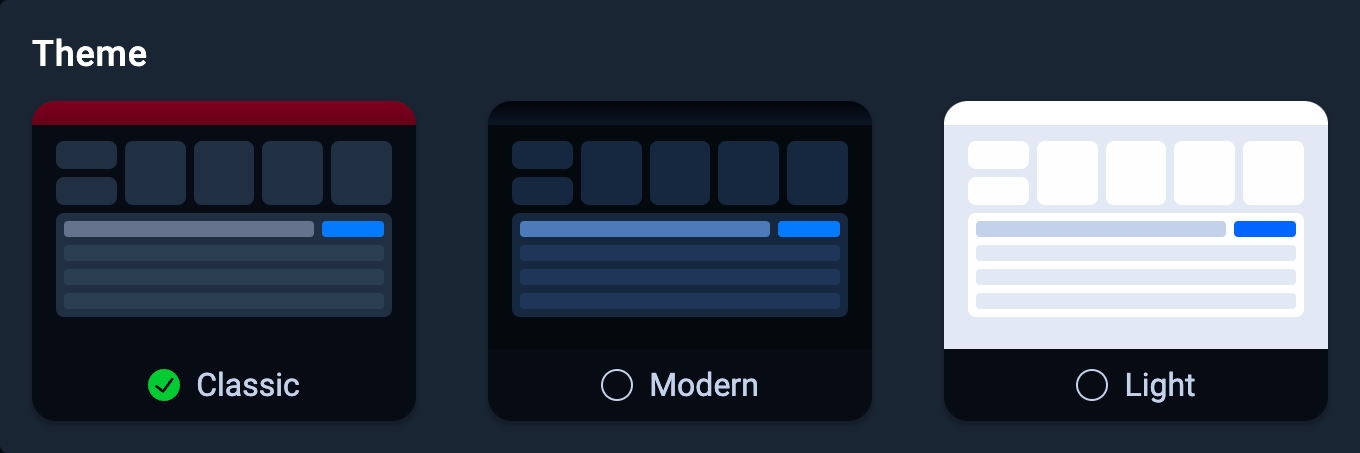
New Color Themes
We've added two new themes for better user experience: "Modern" and "Light."
The "Modern" theme incorporates cooler grays, providing improved contrast and rounded corners for a clean look.
The "Light" theme is designed for users preferring a brighter interface, while still maintaining some design elements from the "Modern" theme.
For those accustomed to our original design, the "Classic" theme remains available and will continue as the default until you opt for a change.
Navigation Bar & In-App Guidance Improvements
We've refined the navigation bar with intuitive icons and improved functionality:
- The ‘Message Bubble' icon now directly links to Chatlio, our live support chat.
- The 'Question mark' icon introduces our in-app guidance.
- Selecting 'Help' links within the portal will open a side panel with guidance, allowing you to view instructions without leaving your current task.
- Options previously found under the 'Question mark’ icon have been moved to the main menu, located below your avatar.
Phishing Impact Test (Beta)
The Phishing Test enables NodeZero to automatically capture and use credentials phished through your organization's Phishing Simulation Tool (KnowBe4, Proofpoint, etc.). It is designed to help you measure and understand the impact of a successful phishing attack within your organization, starting with your most phish-prone employees.
This feature is currently only available to select customers and design partners. If you would like to try out this feature and provide feedback, please reach out to Customer Success.
Features / Enhancements
- CVE-2023-36844: We've added the capability to detect and exploit vulnerabilities in Juniper Junos OS SRX Firewalls and EX Switches. Successful exploitation allows remote command execution as root, granting full access to the device.
- CVE-2023-29489: Cross Site Scripting (XSS) vulnerability identified within cPanel.
- CVE-2023-29298: Enhancement for bypassing Secure Profile and IP address restrictions in targeted Adobe ColdFusion servers.
- CVE-2023-26360: Deserialization flaw leading to unauthenticated RCE on specific versions of Adobe ColdFusion. This exploit works in tandem with CVE-2023-29298, resulting in remote execution as the user running the Adobe ColdFusion service (typically SYSTEM on Windows or www-data on Linux).
- CVE-2023-38646: Metabase open source and Metabase Enterprise versions prior to 0.46.6.4 are susceptible to attackers executing arbitrary server-side commands without needing authentication.
- CVE-2021-42392: Security issue allowing Remote Code Execution (RCE) in the H2 Database Console.
Bug Fixes
- Added additional exception handling for communication errors that occurs when running
digagainst non-DNS servers with port 53 open - Added additional ports and exception handling to services discovered using
DNS SRVrecords. - Added additional error handling when receiving unexpected output when querying LDAP servers as an anonymous user.
- Adjusted the
ADCS Verify Credsmodule to target specific Domain Controllers. - Improved the parsing of Kerberos ticket hashes for non-default encryption types discovered in Kerberoasting attacks.
- Improved base URL calculation used when targeting applications in attacks