2023.01
We are in the process of revamping our user experience. A significant amount of work is going into improving the usability and user experience. That work isn't yet publicly available, but we are collecting feedback from our design partners and beta testers and are excited to share the experience with you in the near future! Until then, below is what we've added to portal in this month's release.
Portal
New Manage Engine Course of Action (COA) card
This COA card enables users to take quick action for testing for the recently released ManageEngine SAML Remote Code Execution weakness in your environment.
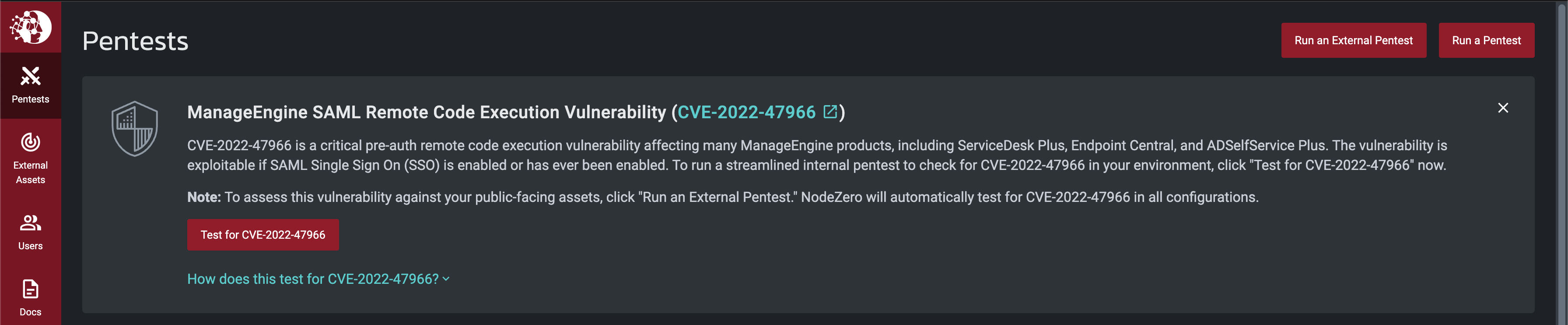 To read more, please see ManageEngine (CVE-2022-47966) Technical Deep Dive.
To read more, please see ManageEngine (CVE-2022-47966) Technical Deep Dive.
NodeZero
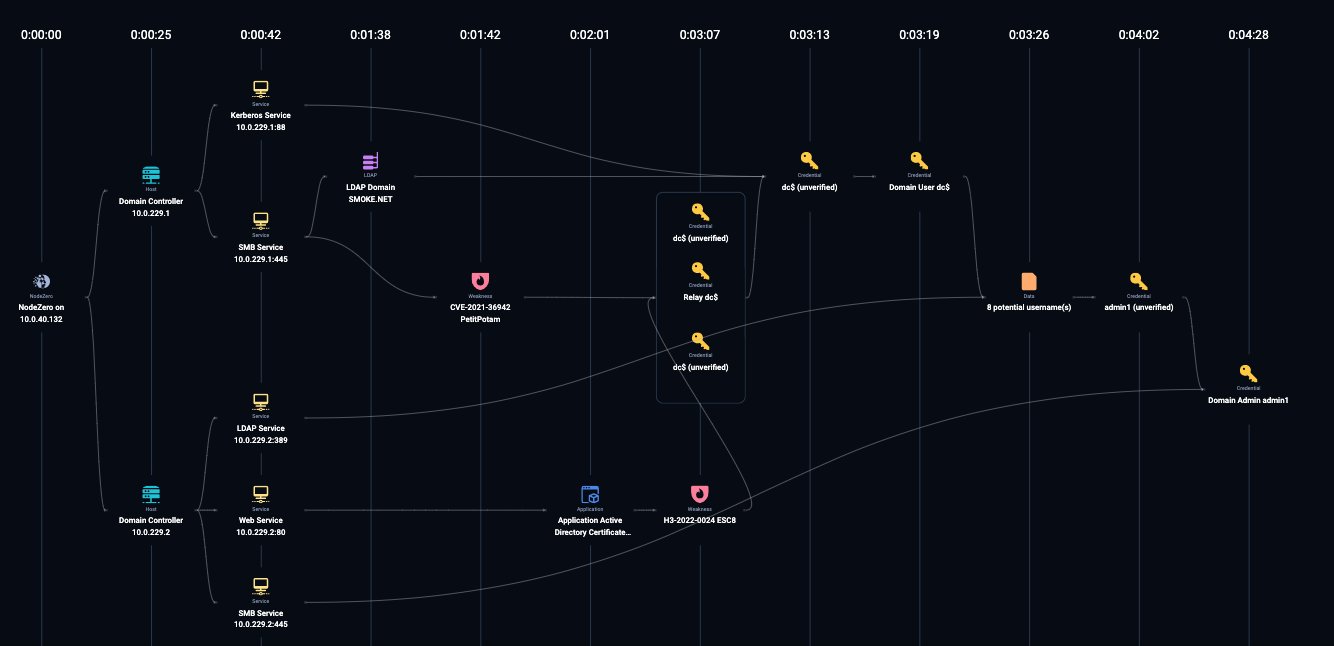
Active Directory Certificate Services (ADCS) Privilege Escalation (ESC8)
Background: In their research papers, Will Schroeder and Lee Christensen found a domain escalation vector based on web endpoints vulnerable to NTLM relay attacks. The escalation vector was dubbed ESC8.
Active Directory Certificate Services(ADCS) is Microsoft's enterprise PKI implementation that integrates with Active Directory. ADCS supports a certificate enrollment web interface that gets exposed on <http://<ADCSSERVER>/certsrv/.> This web interface is vulnerable to a Man-in-the-middle NTLM relay attack and can enable an attacker to gain privileged credentials leading to a full domain compromise.
Once an authentication session is initialized by a victim user/machine, cyanide can relay the authentication material to the vulnerable ADCS server to authenticate. Once authenticated, NodeZero will then request a PKI certificate for our victim account that can be utilized for domain authentication. If successfully done with a DC or admin credential, NodeZero has obtained sufficient authentication material to compromise the domain. Additionally, since certificates are independent authentication material, an attacker can still use these certificates to access the domain even if the user/DC's password is reset.
AWS Attack Content
EC2 Instance Enumeration
NodeZero now enumerates EC2 instances and uses injected/discovered credentials with SSM access to achieve command execution on those EC2 instances
Background:
AWS Simple Systems Manager Agent (SSM Agent) is Amazon software that runs on Amazon Elastic Compute Cloud (Amazon EC2) instances, edge devices, and on-premises servers and virtual machines (VMs). SSM Agent makes it possible for Systems Manager to update, manage, and configure these resources.
Updates to some base severity scores
Increased base severity of public EC2 images, EBS snapshots, and RDS Snapshots from 3.9 to 4.5 (H3-2022-0088, H3-2022-0089, H3-2022-0090)
CISA Known Exploitable Vulnerabilities (KEV)
Added detection and exploitation of known exploited vulnerabilities into NodeZero.
Bugfixes
- Fixed an issue in which NodeZero could report XSS weaknesses that were false positives
- Fixed an issue in which NodeZero would report S3 buckets taken over in a previous pentest (via Subdomain Takeover) as public S3 buckets (H3-2021-0001). They are now re-reported as subdomain takeovers (H3-2021-0002).
- Fixed an External Pentest issue where NodeZero would fail to start when running on an Amazon AMI
- Updated OpenSSL binary to patched version 3.0.7-1 which mitigates CVE-2022-3206, CVE-2022-3786