AD Password Audit
NodeZero® AD Password Audit is an easy way to audit the strength and similarity of user passwords in an Active Directory environment. Read below for motivations, necessary environment configurations, and instructions on running an AD Password Audit.
Motivations for AD Password Audit How to Configure Your Environment How to Run an AD Password Audit
Motivations for AD Password Audit
Reasons to Perform a Password Audit
Weak passwords factor into a number of commonly used attacker techniques:
Attackers take advantage of weak passwords for both initial access and lateral movement.
On the perimeter, it’s common for attackers to target endpoints not enabled for MFA. For cases that MFA is enabled, having a user’s password becomes the first stage to subsequent attacks such as MFA fatigue attacks.
On internal networks, attackers generally don’t need to worry about MFA as there are many endpoints and protocols (e.g. SMB, DCOM/RPC, NTLM) available for abuse that don’t support MFA.
Reasons to Run a Password Audit Regularly
It’s important to audit passwords regularly because the state of the passwords and accounts in Active Directory changes over time.
- Employees join or leave an organization.
- Employees change their passwords. Many organizations have policies in place that require employees to rotate their passwords.
- New data breaches in the wild can expose passwords previously thought to be safe.
Audit passwords regularly
We recommend running an AD Password Audit at least once every three (3) months.
How to Configure Your Environment
This section reviews the prerequisites to running an AD Password Audit. Instructions are given for configuring your environment to ensure the audit can run successfully.
Already configured your environment?
Jump to the section on How to Run an AD Password Audit.
Privileged Account
Prior to running an AD Password Audit, you must have the credentials for a domain user account with DCSync privileges. A domain admin account can be used, but we recommend setting up a separate account with the minimum privileges required.
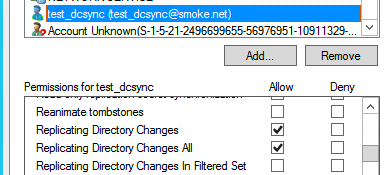
The minimum privileges required are:
Replicating Directory Changes
Replicating Directory Changes All
Replicating Directory Changes in Filtered Set
Configuring EDR to Allow DCSync
EDR software running on the domain controller may block DCSync from taking place. This is a good thing in general as it prevents attackers from using this well-known attack technique. However, for the sake of the AD Password Audit, DCSync needs to be allowed. We recommend consulting your EDR vendor’s documentation for instructions on how to adjust the EDR configuration to enable DCSync. Once you finish running an AD Password Audit, the configuration should be reset to block DCSync again.
Testing DCSync
You can manually verify that DCSync will work using the NodeZero Docker container. On a host where you have already run a NodeZero pentest before, start up an old NodeZero container.
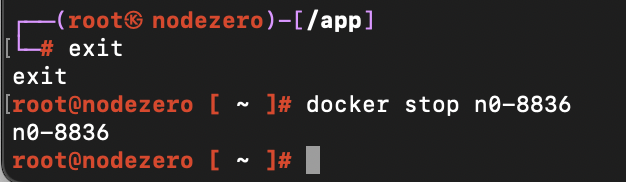
First run docker ps -a to list any existing containers.
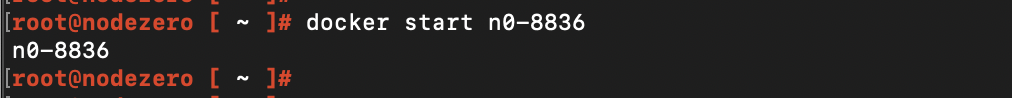
Then run docker start n0-xxxx to start an existing container (substitute n0-xxxx for your container’s name).
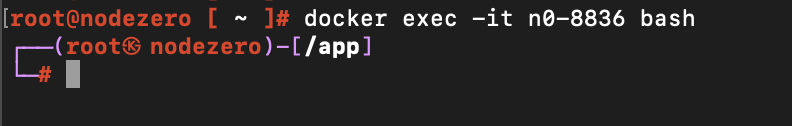
Then run docker exec -it n0-xxxx bash to get a shell inside the container.
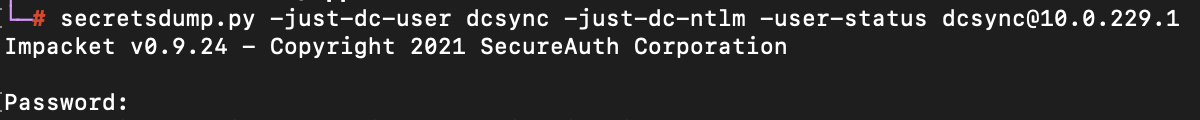
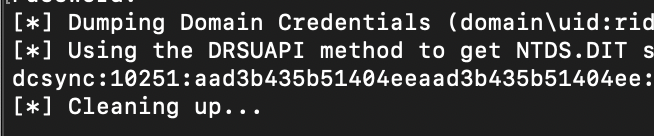
Next, using the privileged account from the previous step, run the secretsdump command to perform a DCSync operation (substitute in your account's username and domain controller IP).
secretsdump.py -just-dc-user <your_dcsync_user> -just-dc-ntlm -user-status <your_dcsync_user>@<domain_controller_ip>
Enter the password for the privileged account.
If the DCSync is successful you should see a successful retrieval of the NTLM hash for just the privileged account.
If the DCSync is not successful, you should recheck your account’s permissions and EDR configuration.
Finally, after testing, exit the shell and stop the NodeZero container. Note, even if you don’t shut it down, the container will automatically shut itself down after ten minutes.
docker stop n0-xxxx
How to Run an AD Password Audit
1. Navigate to Pentests
Navigate to Pentests to start a pentest.
2. Click + RUN PENTEST
Click + RUN PENTEST, then select the Identity Attack Surface category.
Select Active Directory PW Audit to open the configuration for this pentest.
3. Configure the AD Password Audit
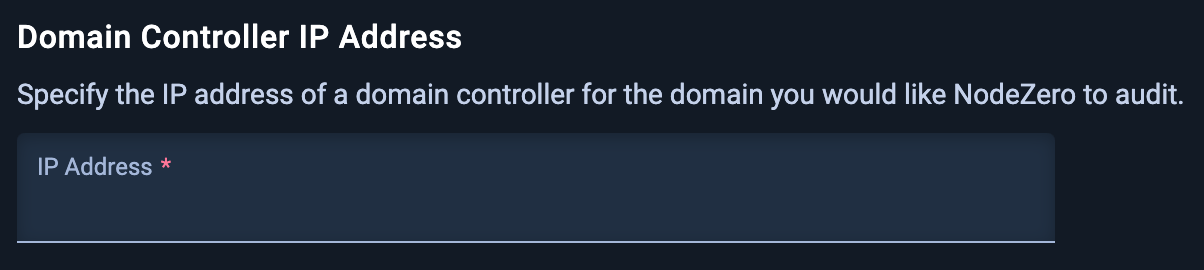
3.1 Name and Domain Controller IP Address
Specify the template, pentest name, and the IP address of a domain controller for the domain you would like NodeZero to audit.
Note
Make sure the IP Address is accessible from where your docker host is deployed.
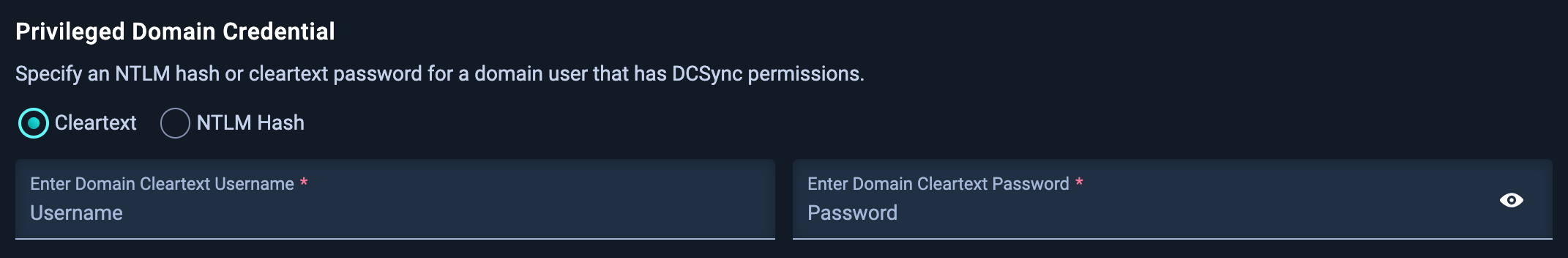
3.2 Privileged Credential
Specify an NTLM hash or cleartext password for a domain user that has DCSync permissions.
DCSync permissions
NodeZero needs DCSync permissions in order to extract the NTDS.dit file from the domain controller. The NTDS.dit file stores Active Directory information about user objects and includes the NTLM hashes for all the users. These NTLM hashes are what NodeZero will attempt to crack. For more information on setting up a credential with the needed permissions, see How to Configure Your Environment
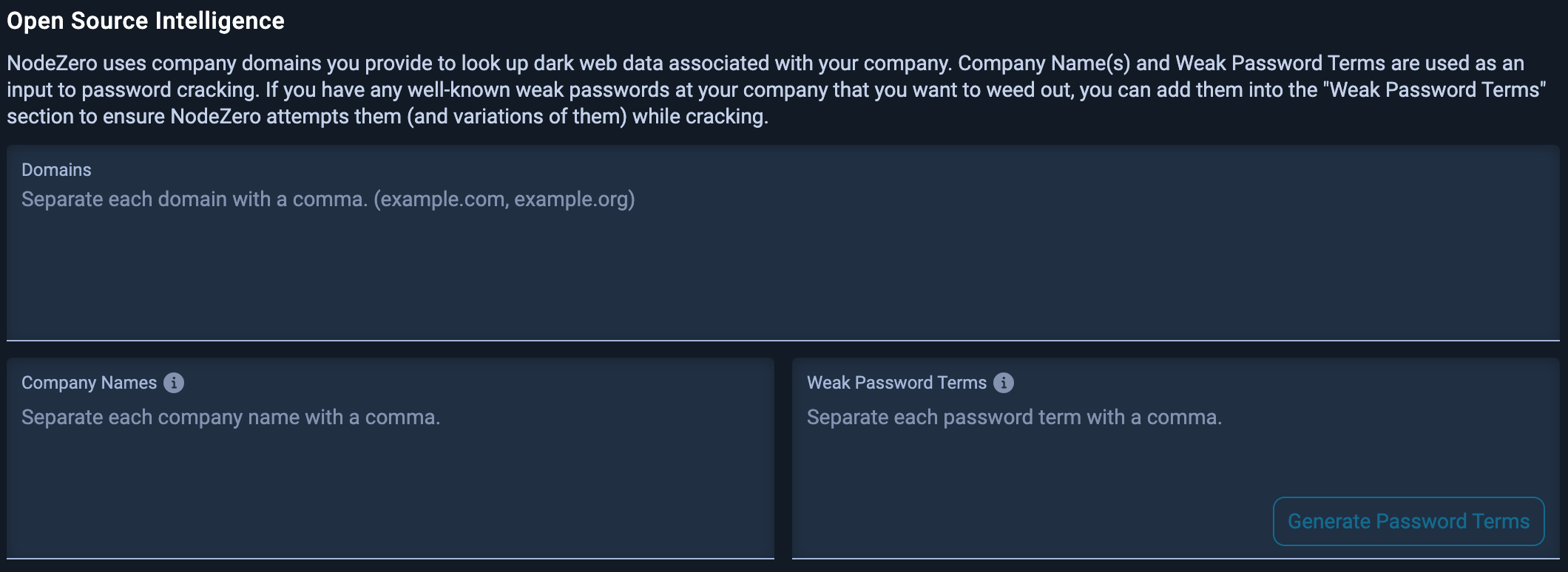
3.3 Add Open-Source Intelligence
The Open Source Intelligence step is important for providing NodeZero context about your company - context that an attacker may be able to leverage to guess weak passwords.
NodeZero uses company domains you provide to look up dark web data associated with your company. Company Name(s) and Weak Password Terms are used as an input to password cracking. If you have any well-known weak passwords at your company that you want to weed out, you can add them into the “Weak Password Terms” section to ensure NodeZero attempts them (and variations of them) while cracking.
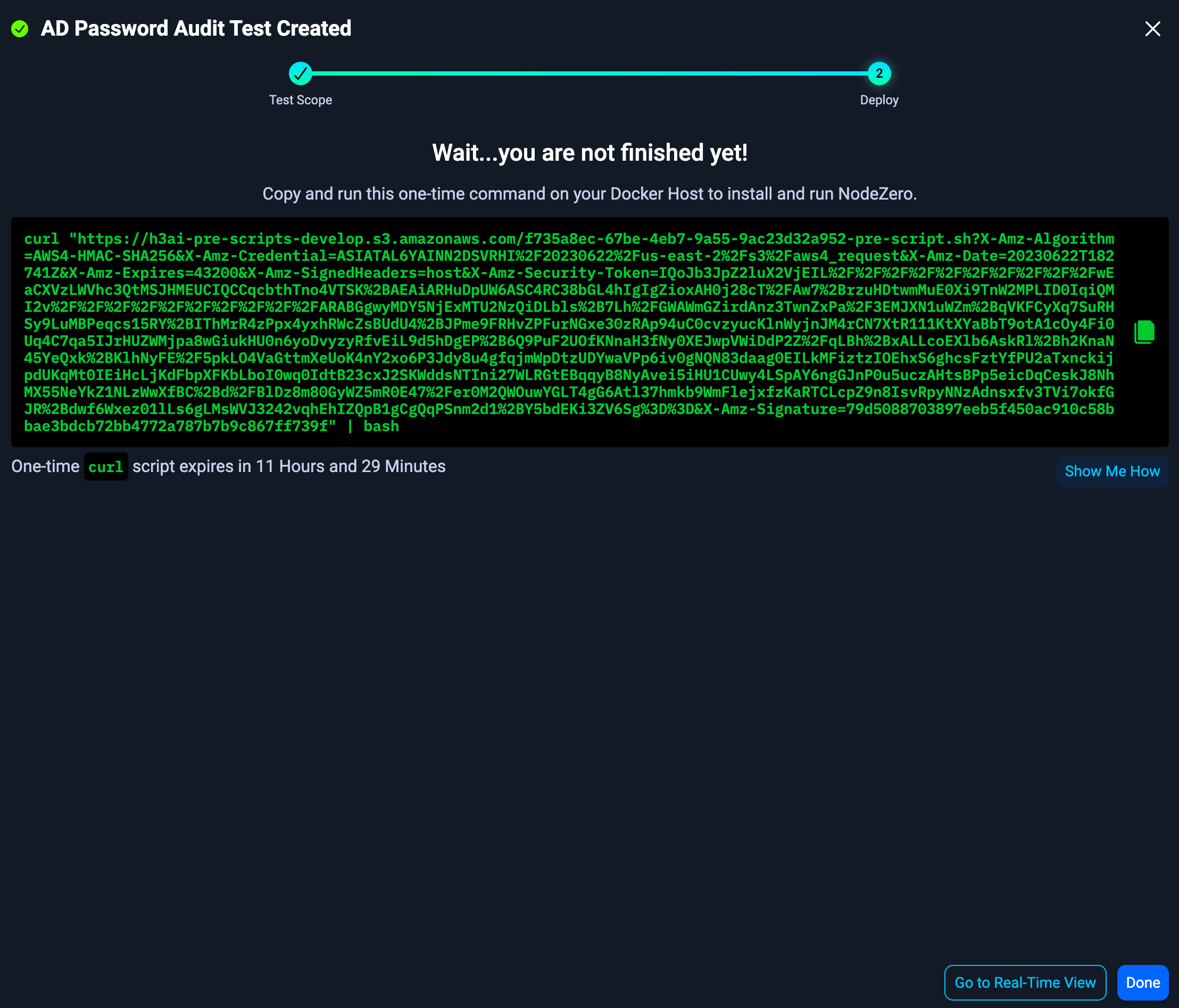
4. Deploy NodeZero
When you're done configuring the pentest, scroll to the bottom of the page and click Run Pentest. This creates the test and brings you to the Real-Time View, where you can copy the NodeZero script to run on your host.
Run the curl script on your NodeZero host to kick off the AD Password Audit. Or, if you are using a NodeZero runner, the audit will kick off automatically on its own.
Don't have a NodeZero host?
See our documentation in Setup NodeZero Host.
The script will validate the Docker installation, download the most up-to-date NodeZero Docker image, and begin the pentest. In the Portal, you will see the status of the pentest transition from Ready to Running.
Successful launch!
Upon completion of the AD Password Audit, NodeZero sends an email to the user that launched it.
How NodeZero Conducts an AD Password Audit
User passwords are stored as NTLM hashes within the Active Directory database file, called NTDS.dit, on domain controllers. To conduct an AD Password Audit, the NodeZero Docker container first performs a remote operation called DCSync to connect to a domain controller and pull these password hashes. NodeZero requires a privileged credential to perform this operation.
User password hashes are transmitted by the NodeZero Docker container to the Horizon3.ai cloud and stored within a secured ephemeral private VPC network for the duration of the audit. The VPC is allocated in real-time when the audit is started and destroyed after the audit completes. All sensitive data, including password hashes, are destroyed at the end of the audit.
Password Cracking
During the audit, NodeZero attempts to crack password hashes using a variety of methods:
- Checking for basic commonly used weak passwords
- Checking for passwords that resemble usernames
- Checking for passwords that resemble well-known contextual terms about a company such as a company’s name or domain name
- Checking for passwords that match or are similar to passwords in dark web data associated with the company
- Checking for passwords that match or are similar to any known breached passwords
- Checking for passwords that match any user-provided custom password terms
Password Reuse
NodeZero also analyzes the population of passwords for password reuse, i.e. cases where two or more users are using the exact same or similar passwords. Password reuse is important to minimize. When users use similar passwords, attackers can easily take a single account compromise and turn it into a multi-account compromise, potentially gaining more privileges and access to data.
Reports
After completing the AD Password Audit, the Fix Action Report can be downloaded by clicking on the download button in the upper-right corner of the summary page.
Viewing Disabled Users
To see disabled users in the AD Password Audit results, go to the "AD Password Audit" page. Click on the 'kebab' menu (three vertical dots) located in the upper-left corner of the results table. From the dropdown menu, select 'View Disabled Users'.
No Passwords were found
If the AD Password Audit fails to display any data upon its completion, verify you have properly configured the injected credential with privileged access. For instructions on configuring the credential, see How to Configure Your Environment.