Run an External Pentest
NodeZero External Pentest is an easy way to gain an additional perspective on your environment. Due to the nature of an external pentest, you must first authorize the discovered assets.
Before getting started, navigate to the NodeZero portal and login with your credentials.
How to Run an External Pentest
To run an external pentest, first create an Asset Group and run Asset Discovery to enumerate external facing assets. When the Asset Discovery completes, you can authorize assets for pentesting and start an external pentest. Follow the documentation step by step or jump to one of the following sections:
Create an Asset Group
1. Navigate to External Assets
To run an external pentest, first create an Asset Group. The Asset Group is used to scope the external pentest.
2. Click Create Asset Group
On External Assets, click + Asset Group to open the asset group configuration.
3. Configure the Asset Group
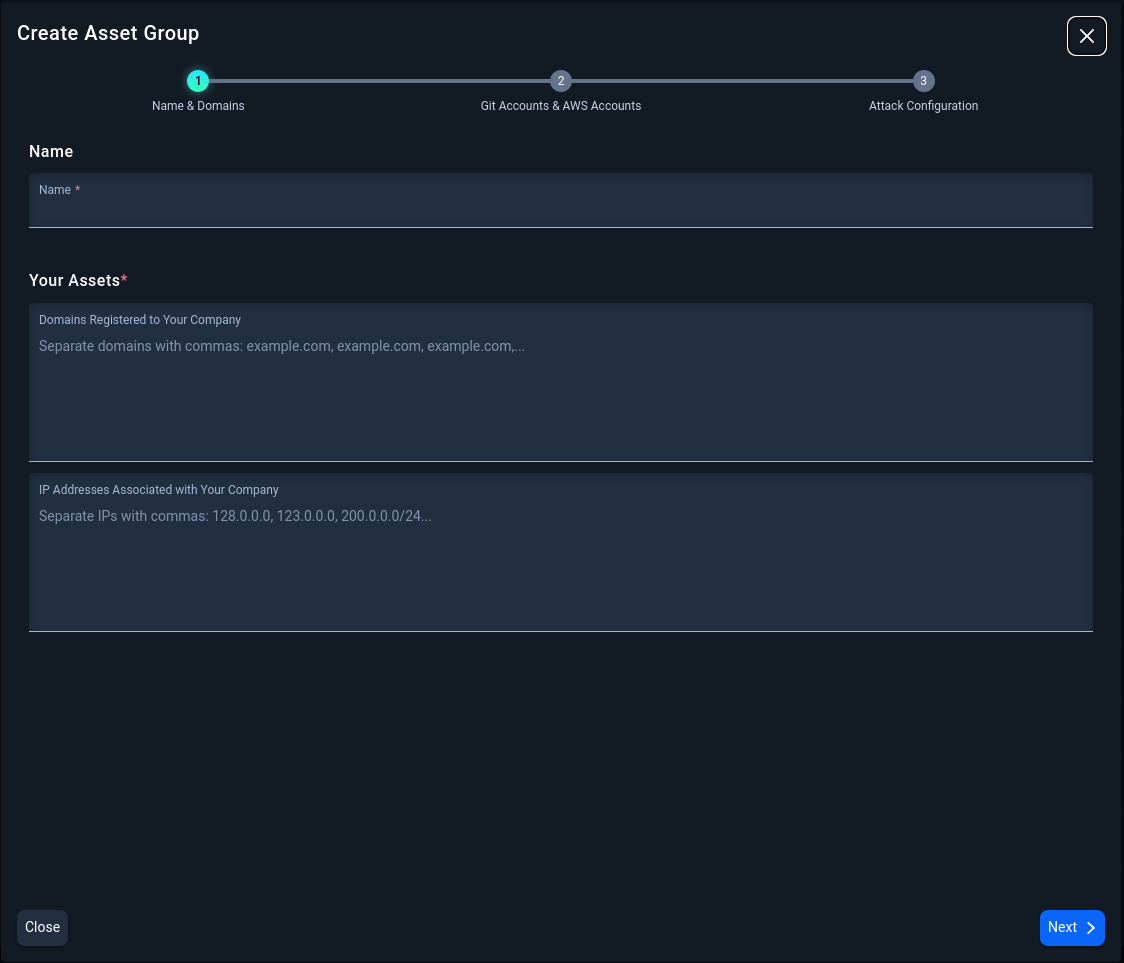
3.1 Set a Scope for the Asset Group
Name the Asset Group and provide company assets as domains, IP addresses, or a combination of domains and IP Addresses. A maximum of 700 domains can be added to the configuration. IP addresses need to be Public IPs only with a maximum input of 3000 entries and formatted using IP/CIDR notation. Please specify a network segment of /20 or smaller (e.g., /22, /23, /24). Both domains and IP addresses should be comma separated. Click Next.
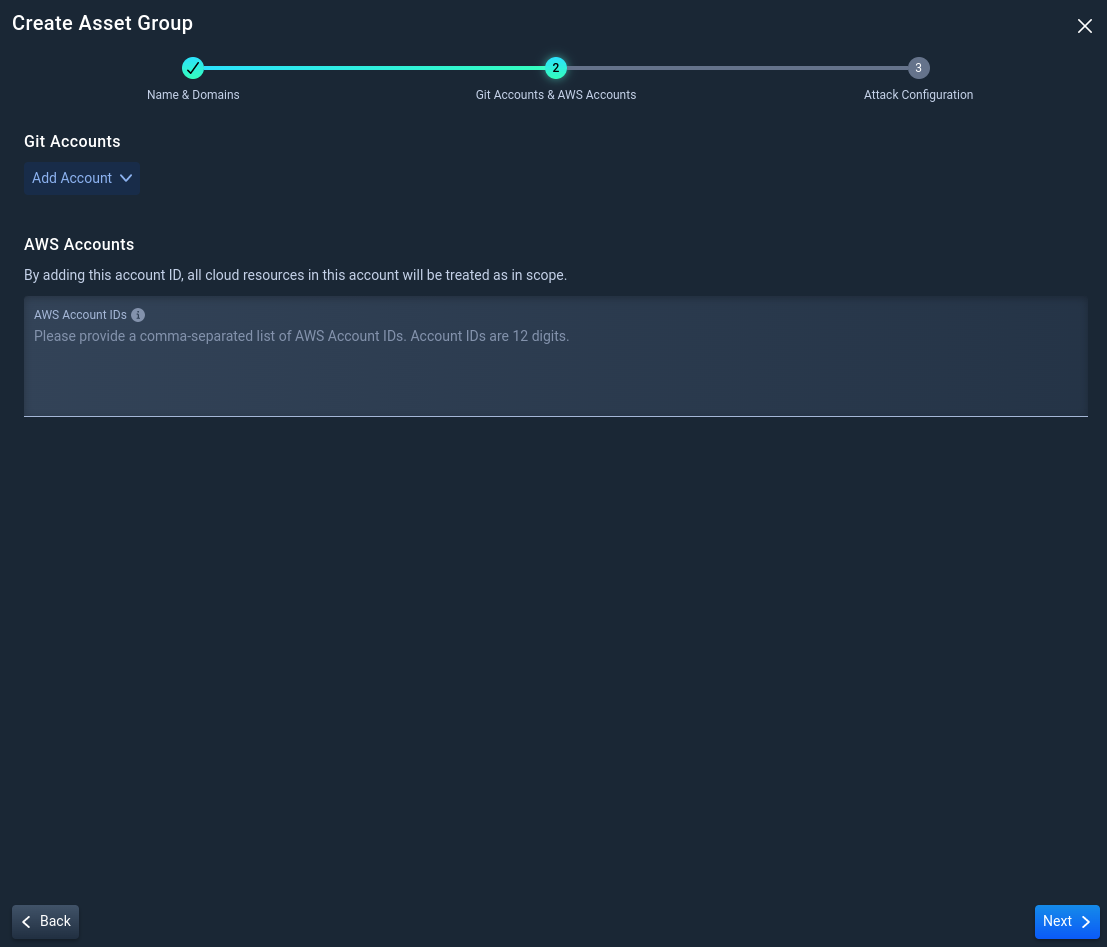
3.2 Optionally, add your Git and AWS Accounts
Listing Git and AWS accounts allows NodeZero to confirm ownership of these accounts and perform a more thorough enumeration of assets.
- To add a Git Account, select +Add Account, select a Git provider, and add the account name.
- To add an AWS Account, type the 12-digit AWS Account ID in the box listed below.
Once satisfied with the accounts, Click Next.
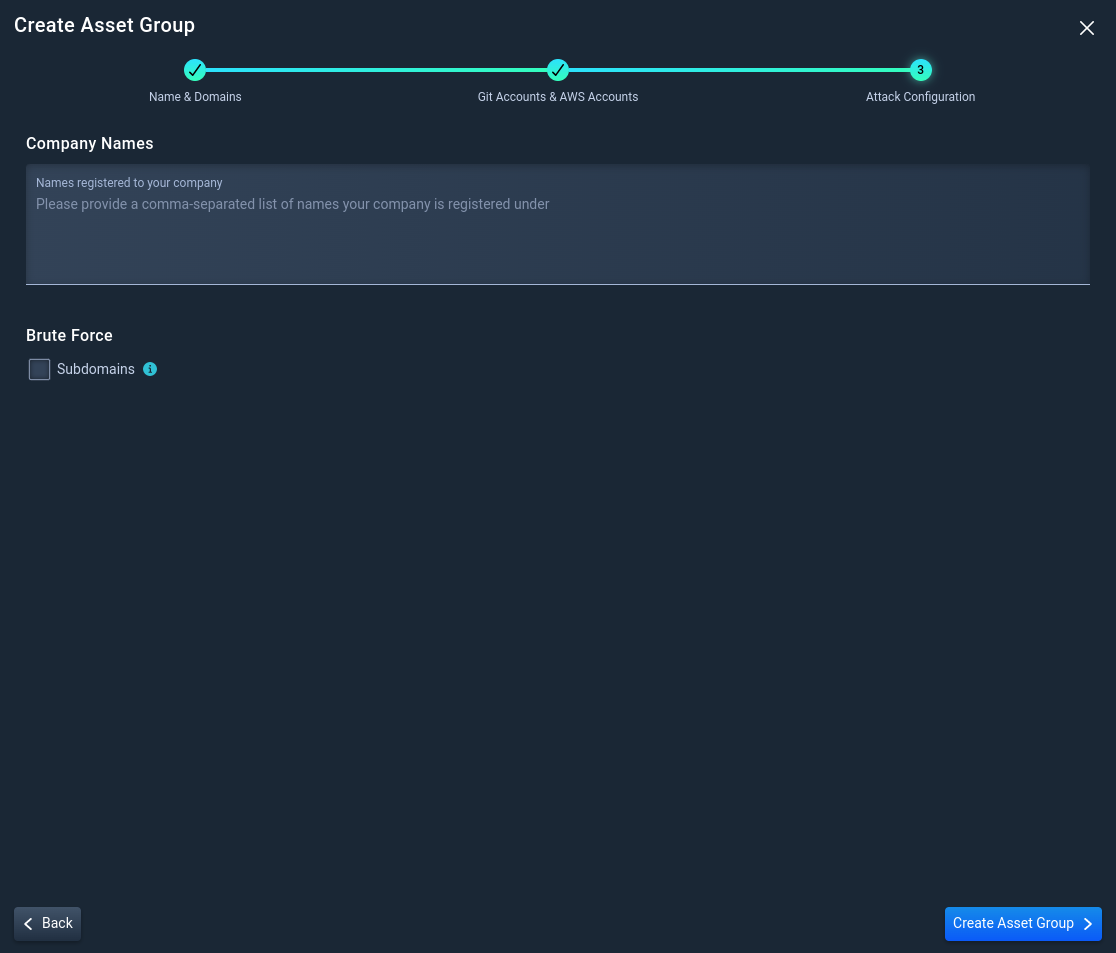
3.3 Attack Configuration Options
- Add company name(s) that NodeZero will use for Open Source INTelligence (OSINT) gathering tools and techniques to harvest company information.
- Enable brute force on subdomains to authorize NodeZero to search for well-known subdomains that may not surface through OSINT discovery.
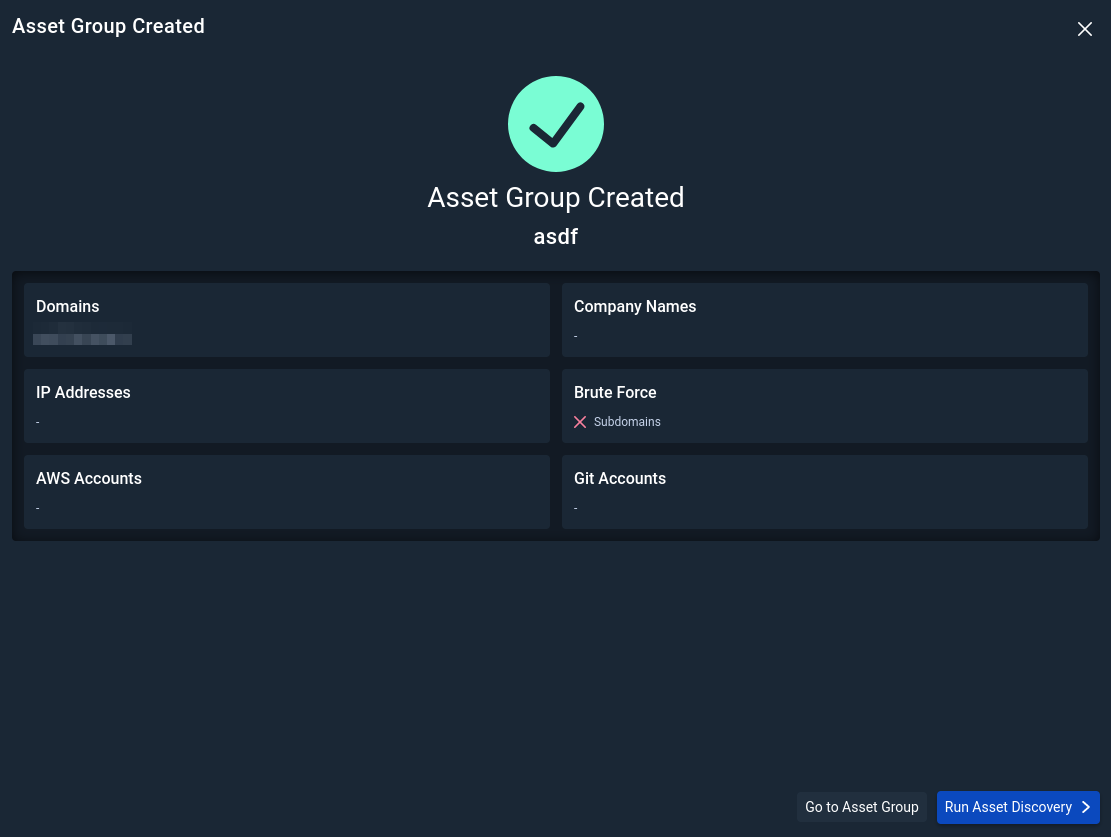
Once satisfied with the configuration options, click Create Asset Group.
Run Asset Discovery
NodeZero’s External Asset Discovery is a passive enumeration capability that leverages DNS, passive website crawling, certificate scraping, and Open Source Intelligence (OSINT) gathering capabilities and services to find all the assets linked to your organization. No exploitation is performed during this operation.
If you just created your Asset Group, review the Asset Group configuration and click Run Asset Discovery. Alternatively, if changes are needed, click Go to Asset Group and click Edit Configuration in the top right.
If you are viewing your Asset Group, click Run Asset Discovery in the top right.
Asset Discovery is in progress
NodeZero sends an email once Asset Discovery finishes enumeration. Return to this documentation when your Asset Discovery is complete to learn how to authorize discovered assets for external pentesting.
Authorize Assets
1. Navigate to External Assets
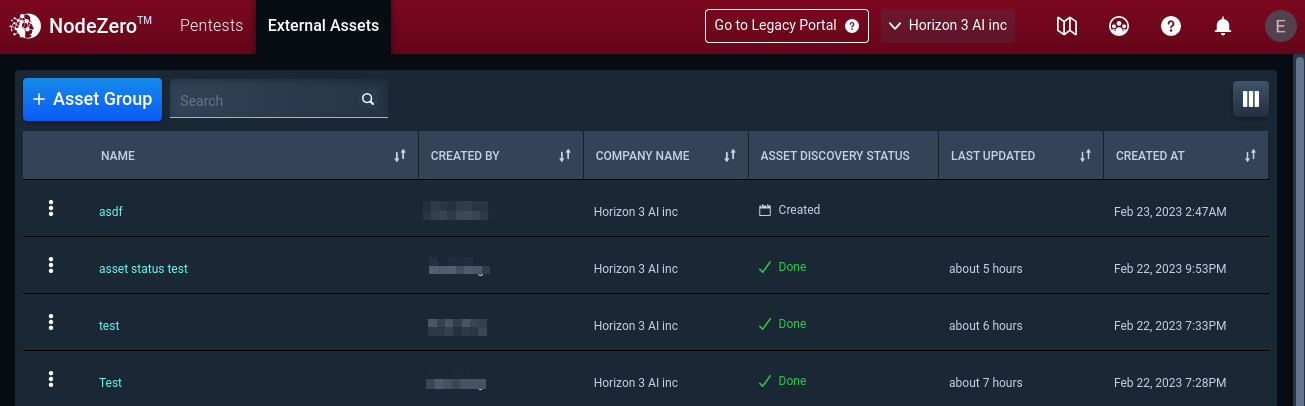
Now that Asset Discovery has been completed, navigate to External Assets to review and authorize assets for external pentesting.
2. Click on the Asset Group
Click the external asset group with the “Done” Asset Discovery Status.
3. Review Asset Discovery
You can check Asset Discovery results and see what has been found.
Rerun Asset Discovery on a routine basis to have the most up-to-date information on the status of your assets.
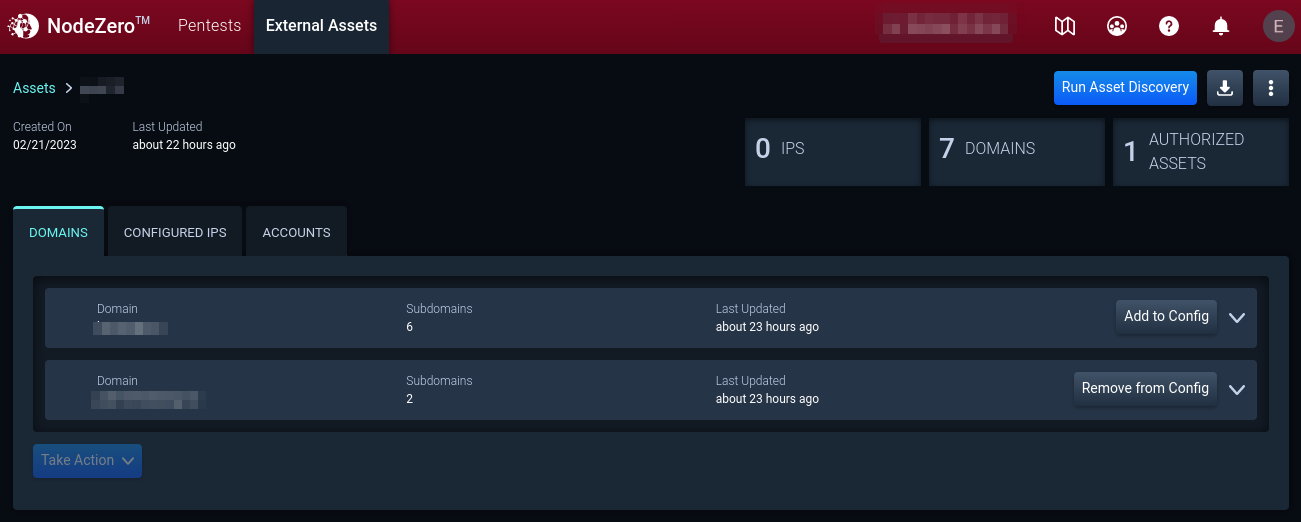
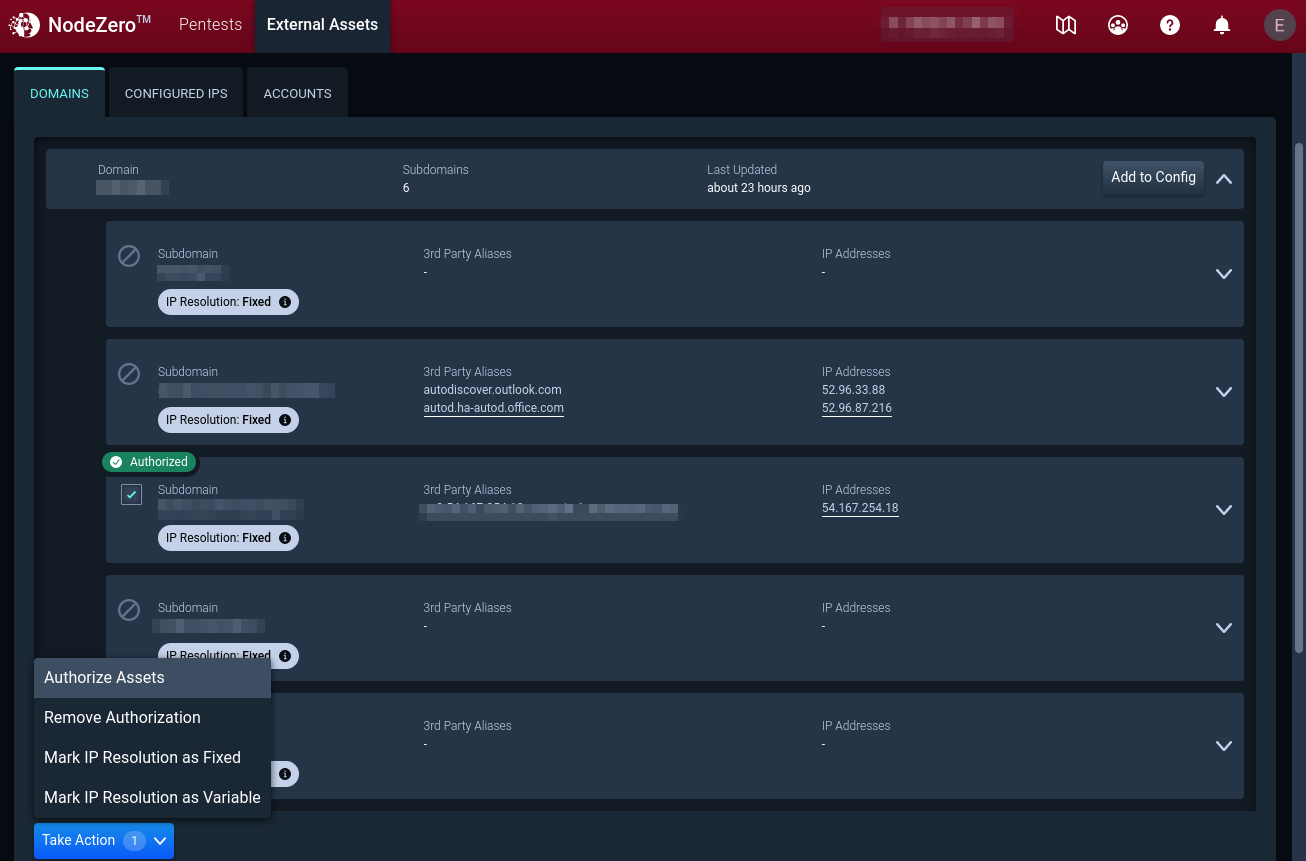
4. Review (Sub-)domains to Authorize Assets
Review discovered (sub-)domains identified during Asset Discovery. To authorize assets for a pentest, select the asset, click Take Action, and then Authorize for Pentest.
Only authorize the assets you are legally permitted to pentest. You are responsible for accurately defining the scope of the Services for both internal and external testing. See Terms and Conditions for more information.
4.1 Asset IP Resolution
During an external pentest, NodeZero uses the asset’s IP Resolution to determine if an asset stays in scope for the pentest. IP Resolution may be marked as Dynamic or Static. By default, assets are set to Static IP Resolution.
Static IP Resolution indicates the IP address resolved from the domain name is not expected to change. Assets labeled Static will be removed from scope if the asset resolves to a different IP address during the External Pentest than it did during the Asset Discovery.
Dynamic IP Resolution indicates the IP address resolved from the domain name may be expected to change over time. Assets labeled Dynamic will remain in scope even if the IP address changes between the Asset Discovery and the External Pentest. An example of a Dynamic asset IP would be AWS assets for which the resolved IP address is controlled by AWS and may change between pentests.
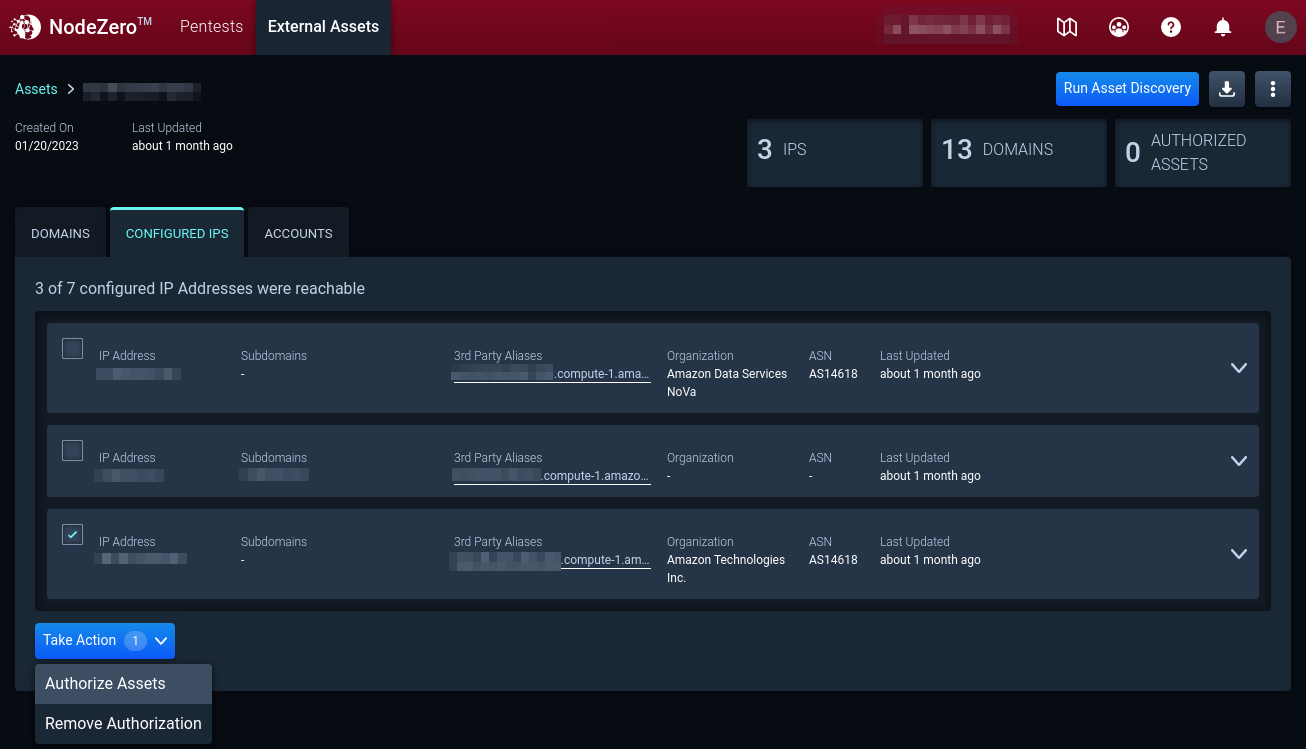
5. Configured IPs
On the Configured IPs tab, view reachable IP addresses in the Asset Group configuration. To authorize an IP address for a pentest, select the IP address, click Take Action, and then Authorize for Pentest.
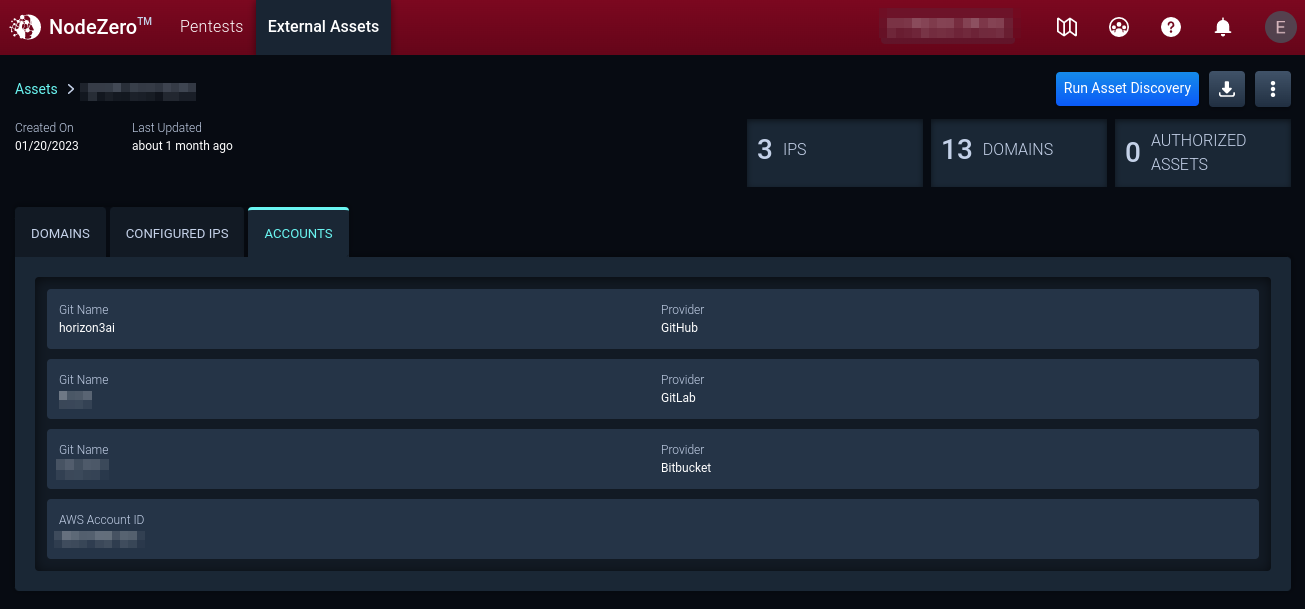
6. Accounts
To add or remove Git or AWS accounts, edit the asset group configuration by clicking the menu button in the top right of the asset group.
Start an External Pentest
1. Navigate to Pentests to Run an External Pentest
Once an Asset Group contains the assets authorized for pentesting, you may navigate to the Pentests page to start an external pentest.
2. Click + Run a Pentest
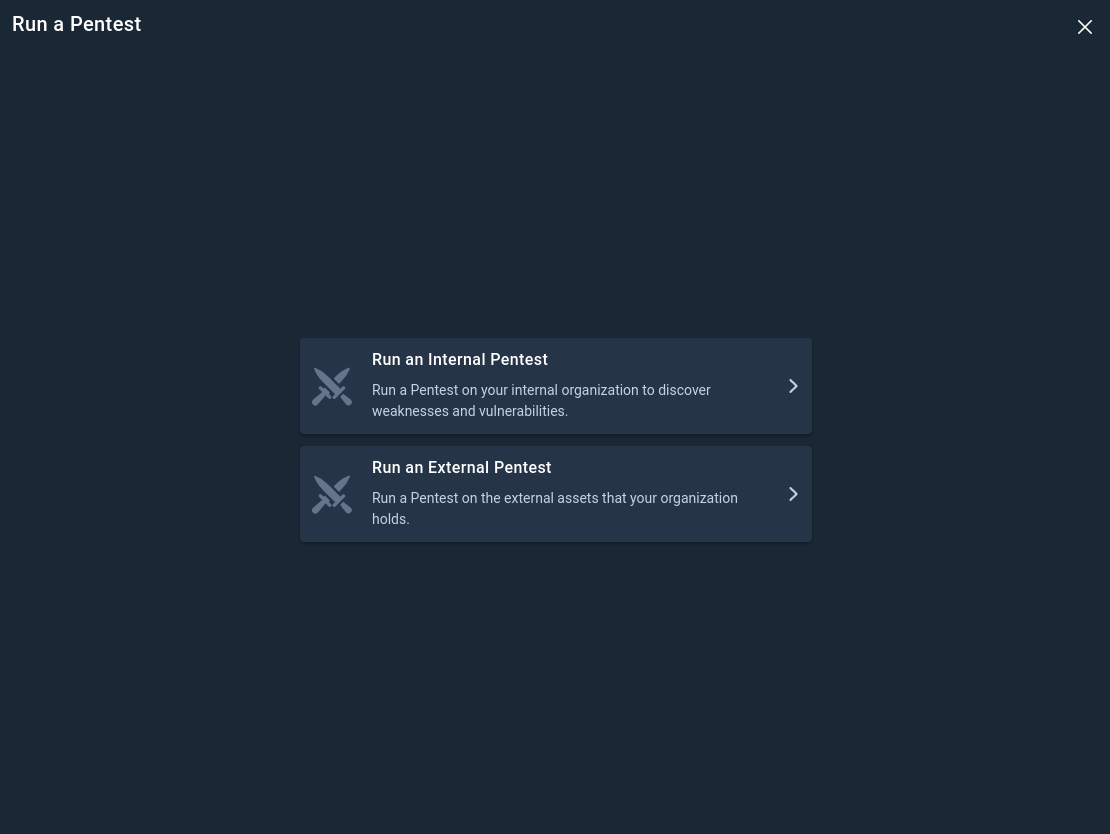
Click + Run a Pentest to open the Pentest Configuration and select External Pentest
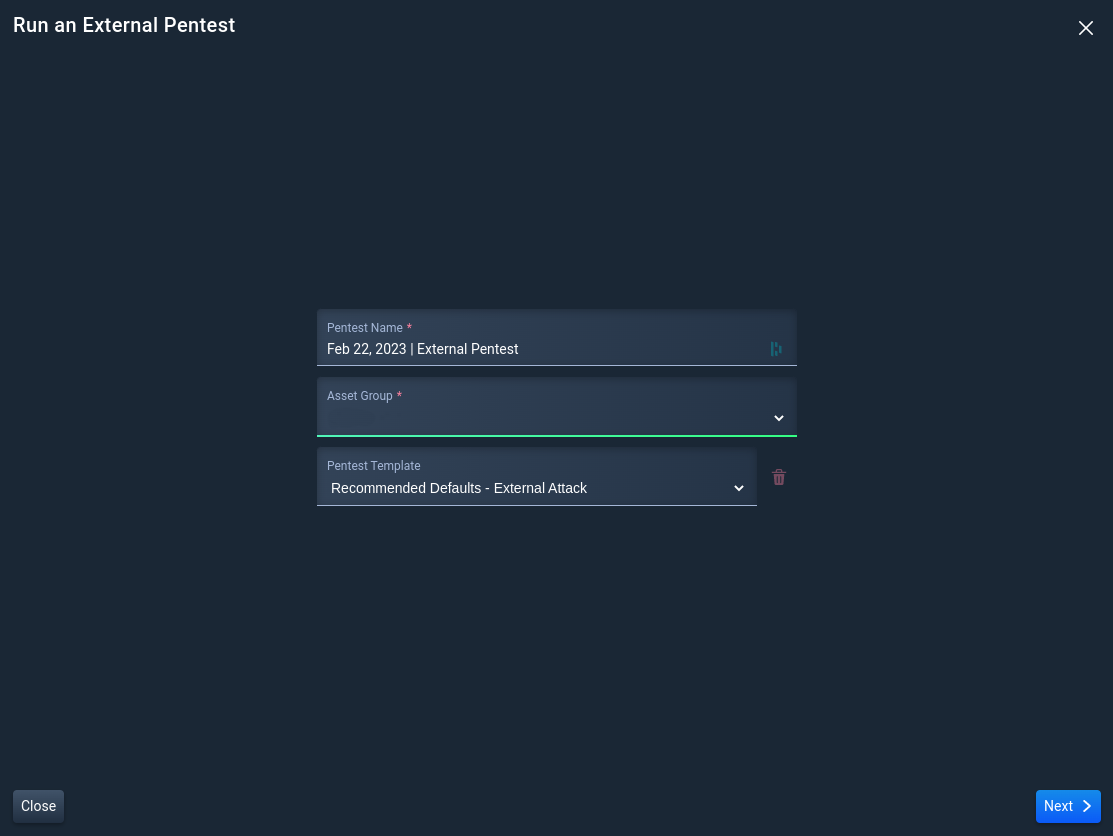
3. Configure the External Pentest
3.1 Set a Scope for the External Pentest
Name the External Pentest, select a pentest template, and select an Asset Group with authorized assets.
If no changes are needed to the template configuration, click Run Pentest to start the pentest now.
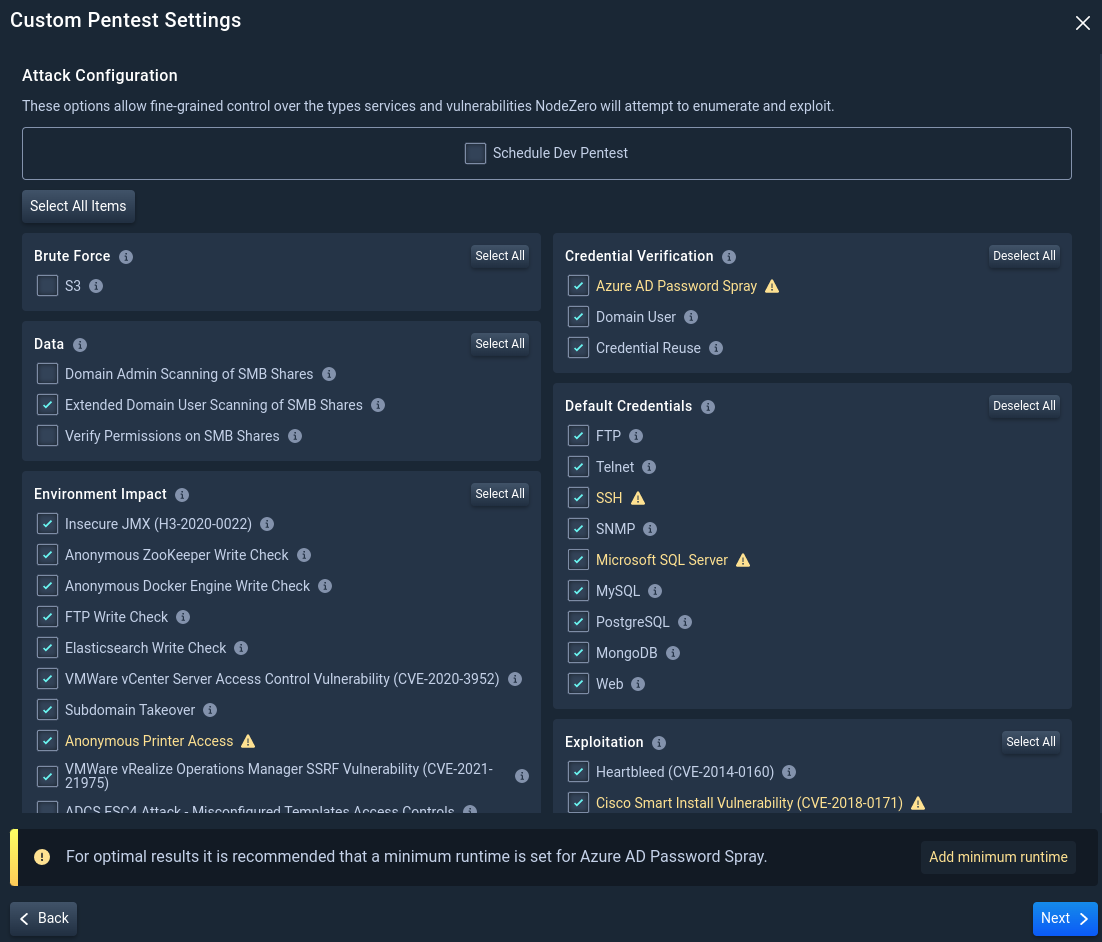
3.2 Advanced Configuration Options
Select the types of services and vulnerabilities NodeZero will attempt to enumerate and exploit. Click Next.
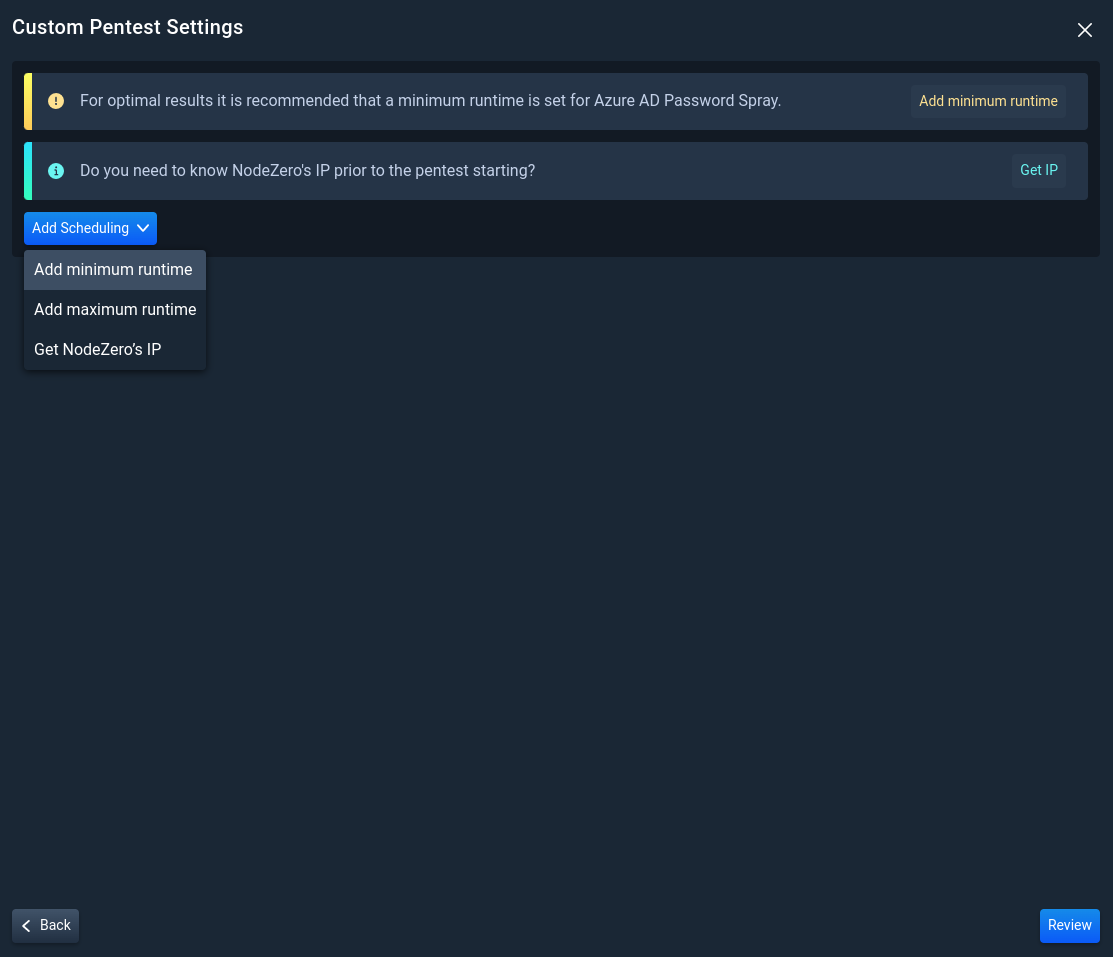
3.3 Additional Pentest Options
Add additional pentest options to further customize your pentest:
- Set minimum or maximum duration limits for the pentest
- Obtain the External Pentest's IP
Then, click Review.
If you select to Get NodeZero's IP, NodeZero will acquire an IP, Pause the Pentest, and notify you that an IP has been acquired. After you have allow-listed the NodeZero IP where necessary, Resume the pentest from the Real-Time View.
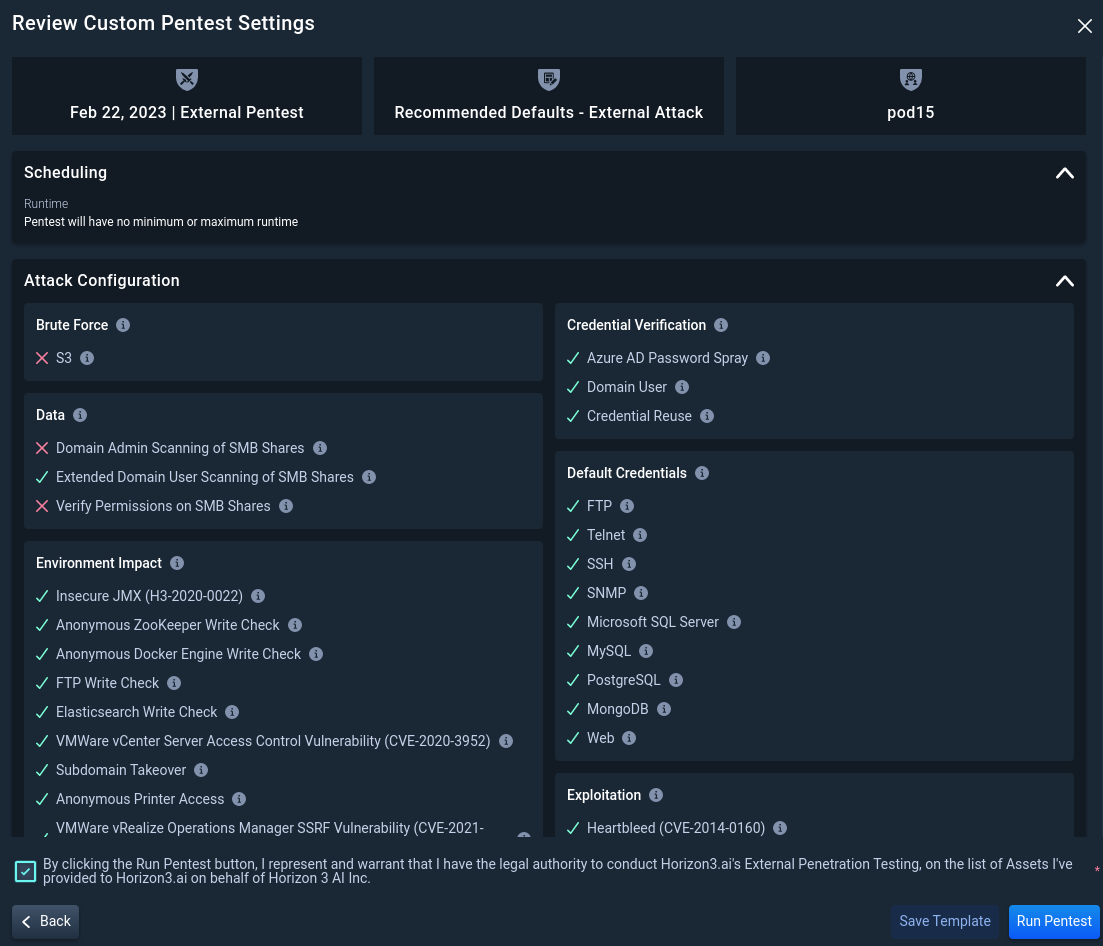
3.4 Review the External Pentest Configuration
Once satisfied with your pentest selections, check the box to indicate you represent and have the legal authority to conduct Horizon3.ai's External Penetration Testing on the list of authorized assets. Then click Run Pentest.
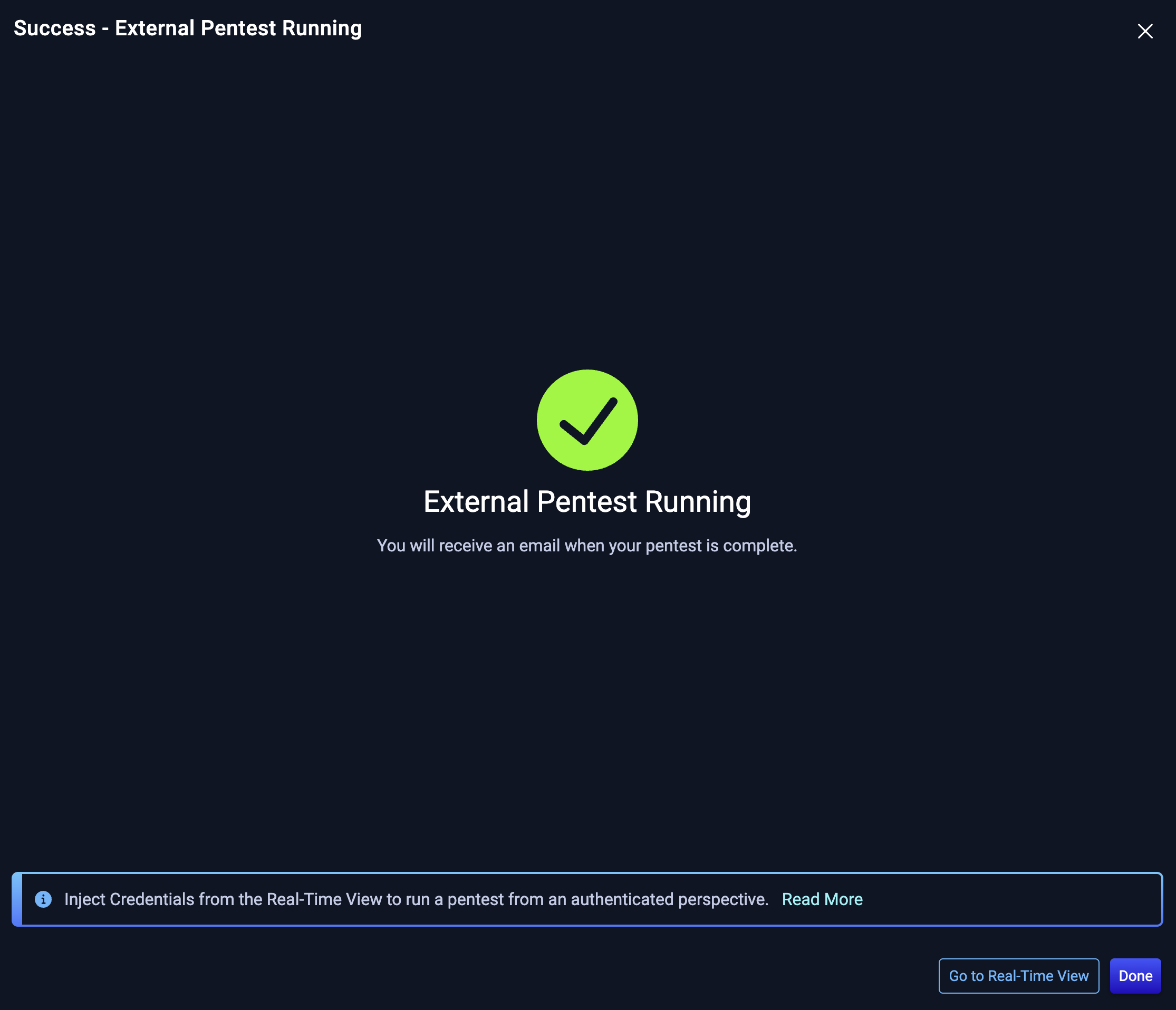
You've started an External Pentest
NodeZero sends an email once the External Pentest completes.
Tip
NodeZero can also run pentests from an authenticated perspective. Go to the Real-Time View and Inject Credentials to see the impact an attacker would have by leveraging compromised credentials!