Deployment Options
The launch point of your NodeZero Host may change based on what you want to learn from the pentest. The following are a few options you may find helpful in making this decision.
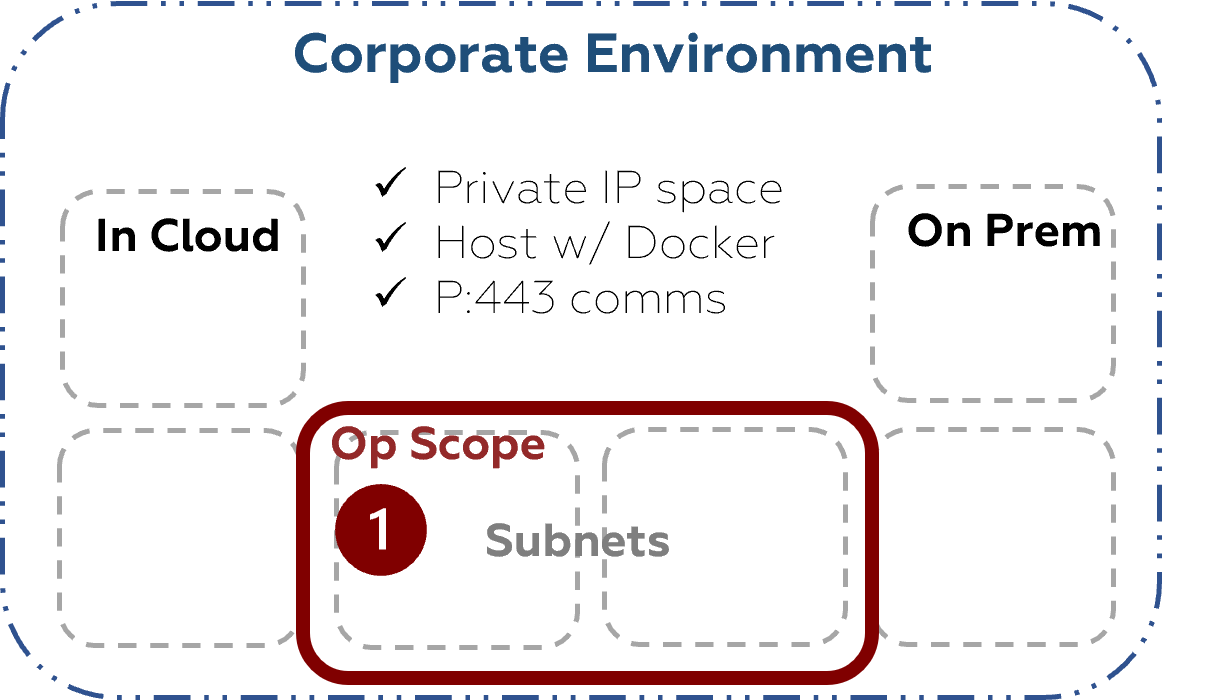
1. Inside Custom Scope
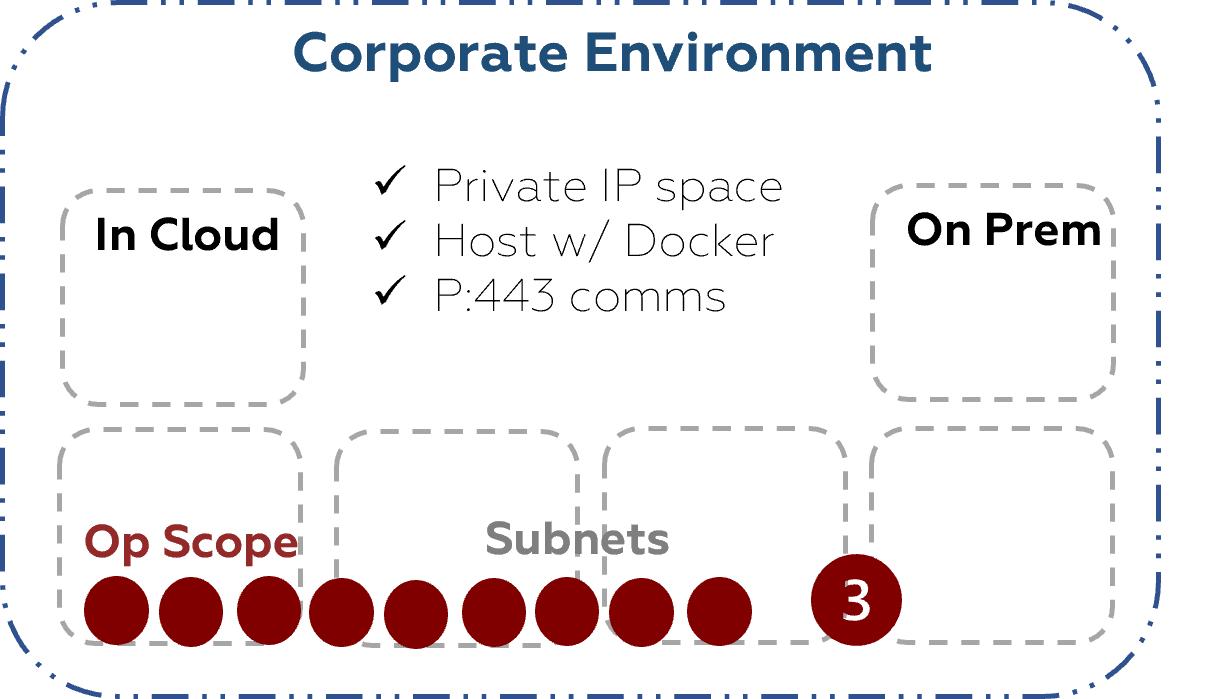
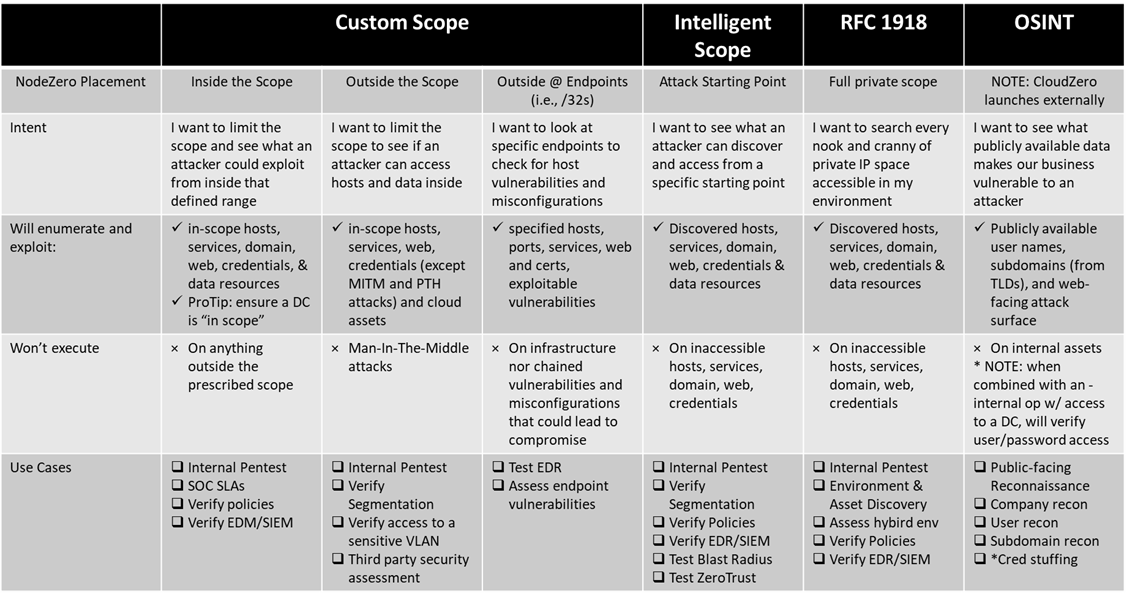
If you want to limit the scope and see what an attacker could exploit from inside a defined range, place the NodeZero host within the scope you want to test. When you configure the scope for your pentest, ensure the NodeZero Host is within one of the specified CIDR range(s) for the test.
Ensure a Domain Controller is in-scope as well, and NodeZero will attempt to exploit any vulnerabilities or misconfigurations on this host, as well as verify weak domain defaults & credentials
This is your high-speed assessment; enabling a lean Find-Fix-Verify loop to initiate an agile security posture
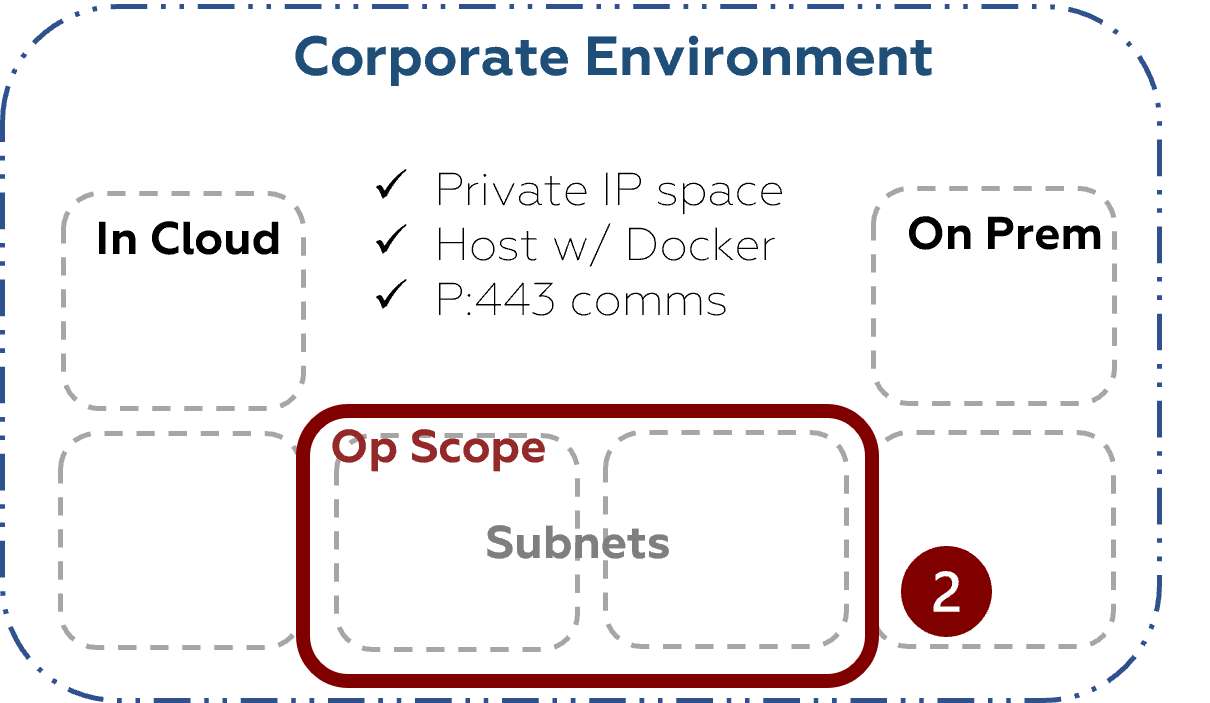
2. Outside Custom Scope
If you wanted an “outside-in” perspective to see if an attacker could access critical data and assets inside a specific scope, place the NodeZero Host outside the scope you want to test. When you configure the scope for your pentest, ensure the NodeZero Host is NOT within the specified CIDR range(s) for the test.
When NodeZero is not in the same IP range as the scope, it will not execute Man-In-The-Middle and pass-the-hash attacks
This is your unrestricted assessment; providing true insight into what is accessible, valuable, and vulnerable from any starting point
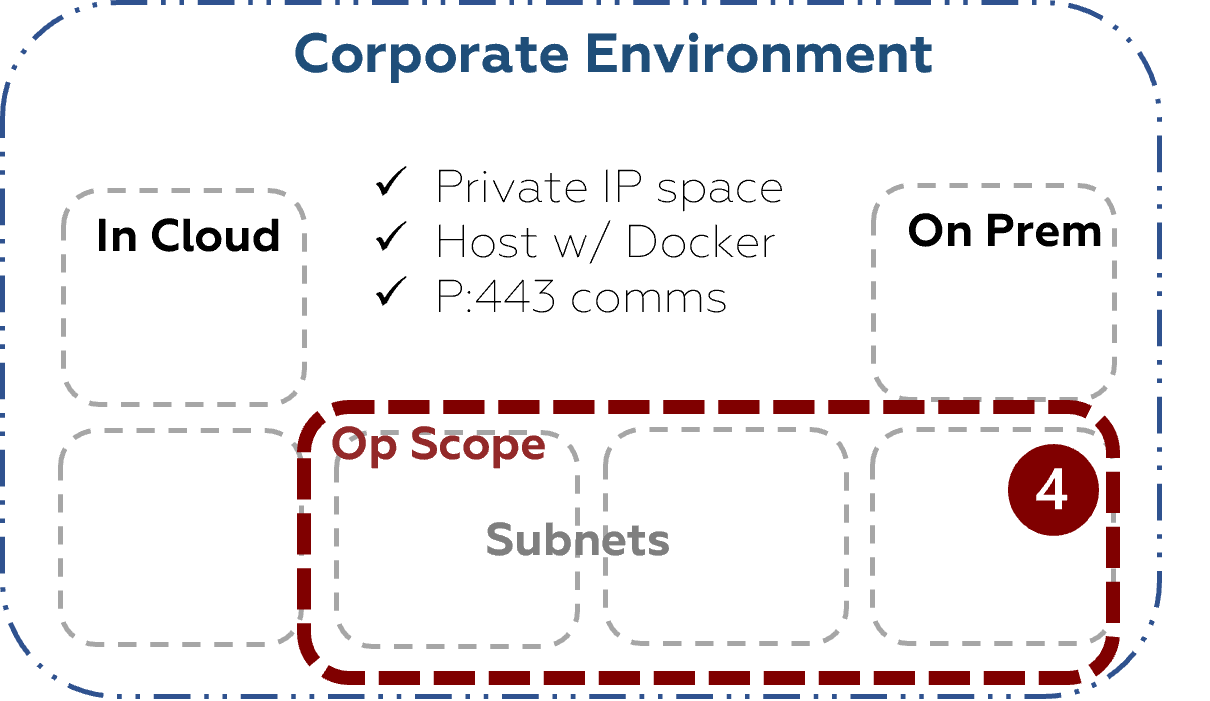
3. Endpoints Only Scope
If you want to quickly verify if the vulnerability you just remediated had the effect you desired, select a single host or range of hosts by /32s. When you configure the scope for your pentest, ensure the NodeZero host has access to the specific host identified by the /32 CIDR range(s) for the test but is NOT within the specified CIDR range(s) for the test.
When NodeZero is not in the same IP range as the scope, it will not execute Man-In-The-Middle and pass-the-hash attacks. Further, with this restricted scope, NodeZero will chain neither weaknesses nor paths as you have limited the scope to a specific endpoint for this assessment
This is your restricted assessment; a quick turnaround op to verify your fix-action was implemented and a vulnerability is now presenting less severity to your attack surface
4. Intelligent Scope
If you wanted to see what an non-credentialed attacker could enumerate and exploit from a specific starting point in your network – a true “black box” pentest – use Intelligent Scope. When you configure the scope for your pentest, leave the “Include” box blank. NodeZero’s host subnet will provide the initial scope and it will expand organically during the pentest as more hosts and subnets are discovered similar to how an attacker would.
This is your proactive assessment; providing true insight into what is accessible, valuable, and vulnerable from any starting point
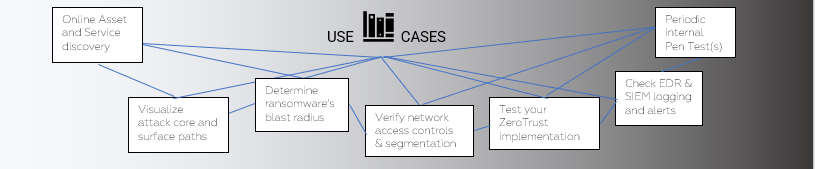
5. All Private IP Scope (i.e., RFC 1918)
Use RFC 1918 to run a private scope pentest, enumerating everything accessible quickly and safely.
When you configure the scope for your pentest, check “Use RFC 1918” and NodeZero will take care of the rest. If there are IP addresses or ranges you do not want to be assessed, add them to the "Exclude" box when configuring the scope for this pentest.
This op may take a bit longer as NodeZero enumerates any IPs and DNS names it can access…including edge routers; if yours are misconfigured for routing private IPs, NodeZero may attempt to enumerate those external private IPs.
if you want to see EVERYTHING, put NodeZero in an unrestricted ACL so it can discover every nook and cranny online in your environment
This is your unrestricted and holistic enterprise assessment–and should be run regularly.
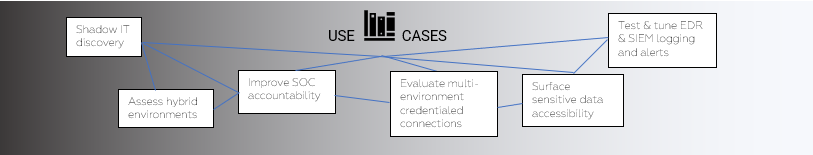
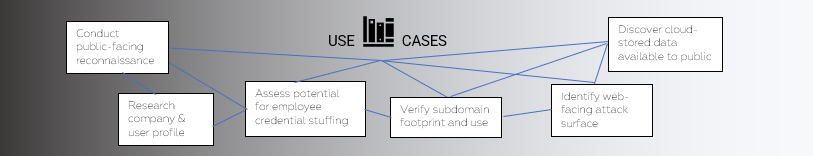
6. OSINT Focused
Available with any of the pentest types is our Open-Source Intelligence (OSINT) assessment, where NodeZero will gather publicly available information to use as part of the pen test. The second step of configuring your pentest offers you the ability to take a true external perspective; your company name will be auto-filled for you, and you can provide TLDs and weak password terms you’d like NodeZero to test with any discovered information.
NodeZero’s OSINT gathering operates outside your environment so NodeZero placement isn’t as critical, however, when combined with an internal pentest with a domain controller in-scope, NodeZero will verify domain users and passwords with those found publicly giving your further insight into your attack surface risk.
This is your external reconnaissance capability to see what attackers see and use to start their campaigns and establish a foothold in your environment
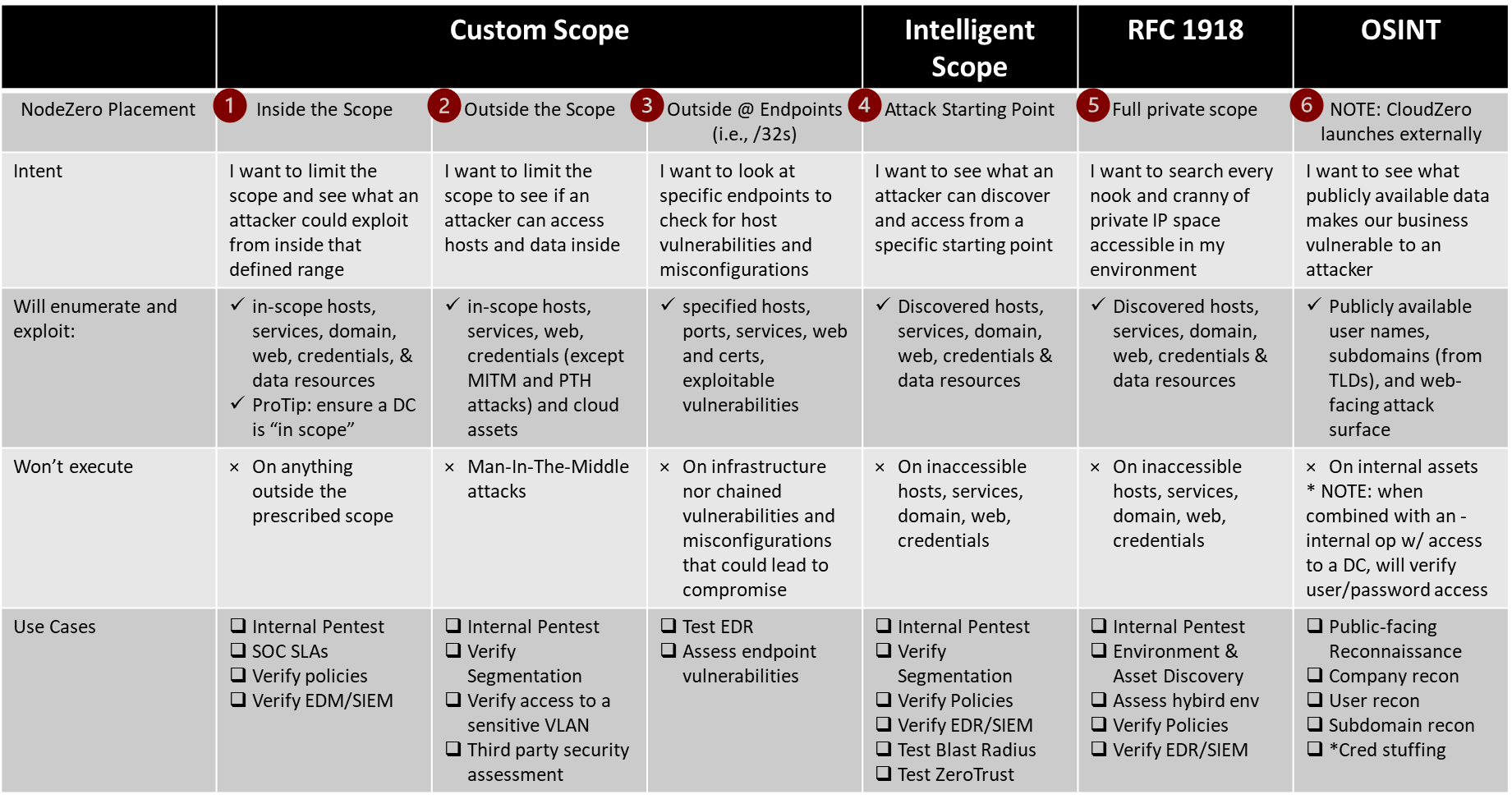
Use this table as a reference for all your pentest operations!